MODERATORS
5 stars based on
44 reviews
Yesterday we learned from new Snowden leaks that the NSA is working to build a quantum computer. The Washington Post broke the story with the rather sensationalist headline, NSA seeks to build ripemd160 bitcoin minerals computer that could crack most types of encryption.
Naturally, this raised much concern among the new Bitcoiners on Reddit and Facebook. Nevertheless, this seems like a good time to discuss the implications of ripemd160 bitcoin minerals computing with respect to the future of Bitcoin. Strings of bits can be combined to produce data that is readable by humans.
Any calculations that need to be performed with the bits are done one at a time. Quantum computers, ripemd160 bitcoin minerals the other hand, use the various states of quantum particles to represent quantum bits qubits. For example, a photon spinning vertically could represent a 1, while a photon spinning horizontally could represent a 0. But photons can also exist in a rather weird state called superposition. What this means for practical purposes is while a traditional computer can perform only one calculation at a time, a quantum computer could theoretically perform millions of calculations all at once, improving computing performance by leaps and bounds.
This is where you just keep checking different keys until you eventually find the right one. Given enough time, you could brute force any encryption key. The problem is it would take billions or trillions of years for a modern computer to brute force a long encryption key. But surely quantum computers could do this right?
Ripemd160 bitcoin minerals of the consequences of the second law of thermodynamics is that a certain amount of energy is necessary to represent information. To record a single bit by changing the state of a system requires an amount of energy no less than kT, where T is the absolute temperature of the system and k is the Boltzman constant.
Stick with me; the physics lesson is almost over. To run a computer any colder than the cosmic background radiation would require extra energy to run a heat pump.
Now, the annual energy output of our sun is about 1. This is enough to power ripemd160 bitcoin minerals 2. If we built a Dyson sphere ripemd160 bitcoin minerals the sun and captured all its energy for 32 years, without any loss, we could power a computer to count up to 2 About a hundred times as much energy would be released in the form of neutrinos, but let ripemd160 bitcoin minerals go for now.
Ripemd160 bitcoin minerals all of this energy could be channeled into a single orgy of computation, a bit counter could be cycled through all of its states. These numbers have nothing to do with the technology of the devices; they are the maximums that thermodynamics will allow.
Inmathematician Peter Shor demonstrated an efficient quantum algorithm for factoring and calculating discrete logarithms that would break public-key encryption when used with a quantum computer. Traditional symmetric-key cryptography and cryptographic hash functions would still be well out of range of quantum search algorithms. It would be much worse if SHA were to go down.
At the moment, billions of dollars have been spent on custom computer chips that do nothing but perform SHA calculations. If SHA were to go down, those custom chips would turn into expensive paperweights.
If that happened suddenly as opposed to allowing for a smooth transition to another hash functionit would be pretty catastrophic.
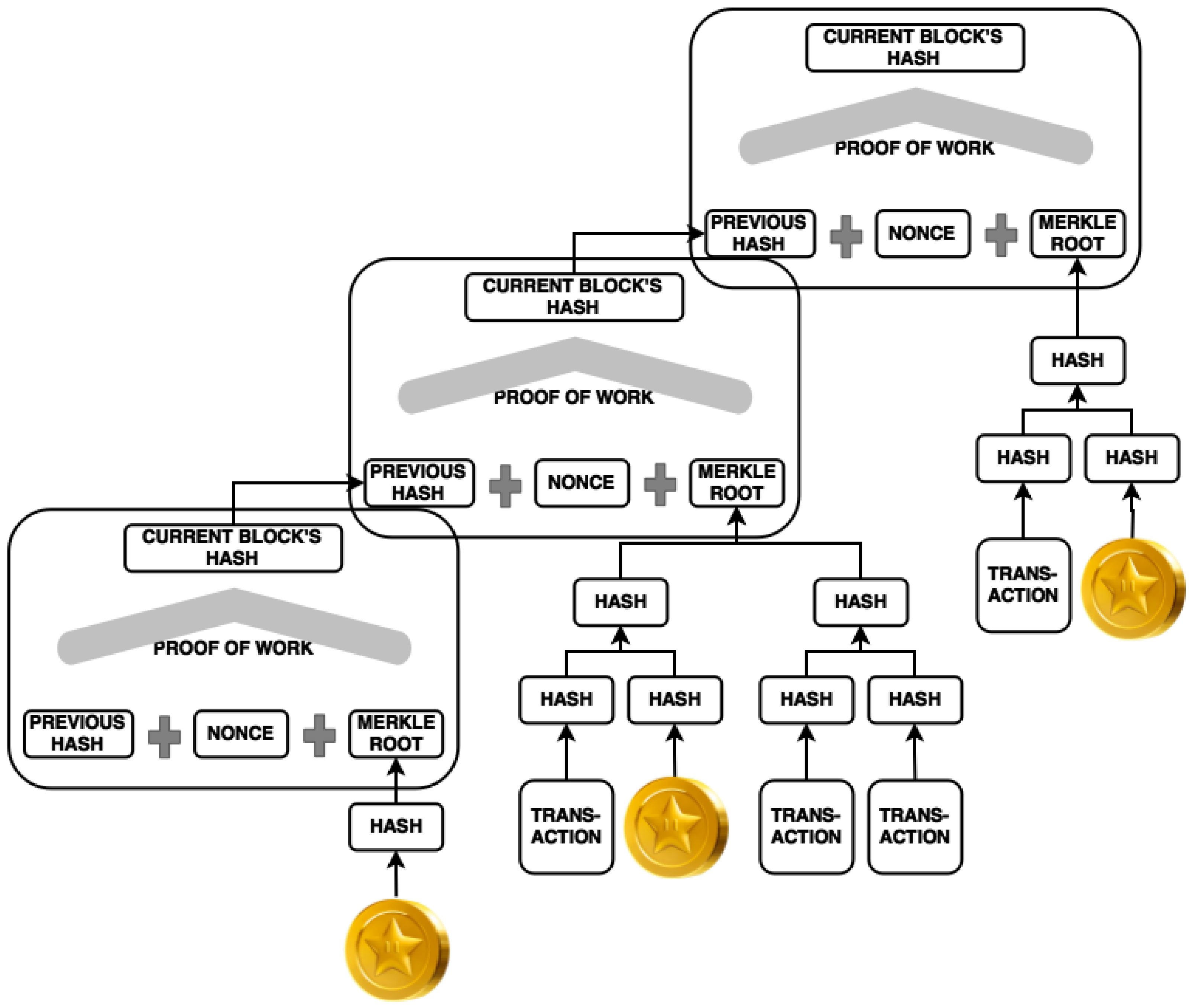
A sudden switch to another hash function would significantly compromise security and likely cause the price to tank. In Bitcoin, you keep the private key secret and use it sign your transactions, proving to the network that you own the bitcoins associated with a particular bitcoin address.
The network verifies your signature by using the corresponding public key. While you share your Bitcoin address with others so that they can send you bitcoins, your Bitcoin address is only a hash of your public key, not the public key itself.
What does that mean in English? A hash function is a one-way cryptographic function that takes an input and turns it into a cryptographic output. A Bitcoin address is calculated by running your public key through ripemd160 bitcoin minerals hash functions as follows:. However, you do have to broadcast your public key to the network to make a transaction, otherwise there is no way to verify your signature.
What this implies is that in the face of an NSA quantum computer all Bitcoin addresses would have to be considered one-time use addresses. While this ripemd160 bitcoin minerals inconvenient, ripemd160 bitcoin minerals would buy the developers enough time to swap out ECDSA for a quantum-resistant digital signature scheme.
This section is going to be a little technical but hopefully not too difficult for beginners to follow. There are several different types of post-quantum public-key encryption systems: As I already mentioned, cryptographic hash functions are presumed to be quantum-resistant.
Given that, it should be possible to build a replacement digital signature scheme for ECDSA using only hash functions. This set of random numbers will serve as the private key. Finally, check to make sure these hashes match the hashes in the public key that correspond with the message digest. So there you have it, a quantum-resistant digital signature scheme using only hash functions.
Only the person in possession of ripemd160 bitcoin minerals random numbers in the private key could have generated a signature that hashes to the public key when compared to the digest. The reason for this is because you are essentially ripemd160 bitcoin minerals half of your private key with each signature.
If you were to sign multiple messages, ripemd160 bitcoin minerals private key would be completely compromised. If this were used in Bitcoin, you still could only use each Bitcoin address once.
Equally problematic, the key sizes and signatures are ridiculously large. The private and public keys are 6, bytes compared to 32 and 64 for the ECDSA private and public keys. And the signature is 3, bytes compared to bytes. Bitcoin already has issues with scalability, increasing the key and signature sizes by that much would make the problems much worse. The Lamport private key can be dramatically reduced in size by generating the random numbers from a single random seed.
There is another one-time signature scheme called Winternitz signatures that has the potential to reduce key size but at the cost of hash operations. The Merkle Signature Scheme combines the one-time signature scheme either Lamport or Winternitz with a Merkle tree also called a hash tree. This allows us to use one public key to sign many ripemd160 bitcoin minerals without worrying about compromising security. To do this, the public keys are paired together, hashed, then the hashes are concatenated together and hashed again.
The hash at the very top of the ripemd160 bitcoin minerals the Merkle root is the Merkle public key. This massively reduces the public key size from 6, bytes in the Lamport signature to only 20 bytes, the length of a single RIPEMD hash. To calculate a signature, you select one of your Lamport key pairs and sign the message digest just like before.
This time, the signature will be the Lamport signature plus each one of leafs in the Merkle tree leading from the public key to the root. To verify the Merkle signature one would just verify the Lamport ripemd160 bitcoin minerals, then check to make sure the leafs hash to ripemd160 bitcoin minerals Merkle public key. If so, the signature is valid. First, the public and private keys are reduced to 20 bytes from 6, bytes. Also, you can create multiple signatures per public key.
But there is still a major draw back. The more messages you want to sign with your public key, the larger the Merkle tree needs to be. The larger the tree, the larger the signature. Eventually the signature starts to become impractically large, especially for use in Bitcoin.
MSS has ripemd160 bitcoin minerals known for over 30 years and has remained essentially unscathed despite extensive cryptanalysis.
However, most of the improvements to it have come in the last five years or so. In my brief survey of the literature, it seems a couple signature schemes by Buchmann, Dahmen, Klintsevich, et.
Two of the cryptographers behind this signature scheme are authors of a textbook on post-quantum cryptography. GMSS in particular offers virtually unlimited signature capacity at 2 80 signatures but with slower performance in others areas compared to CMSS. They accomplishes this ripemd160 bitcoin minerals breaking the system ripemd160 bitcoin minerals into separate Merkle trees of 2 n leafs.
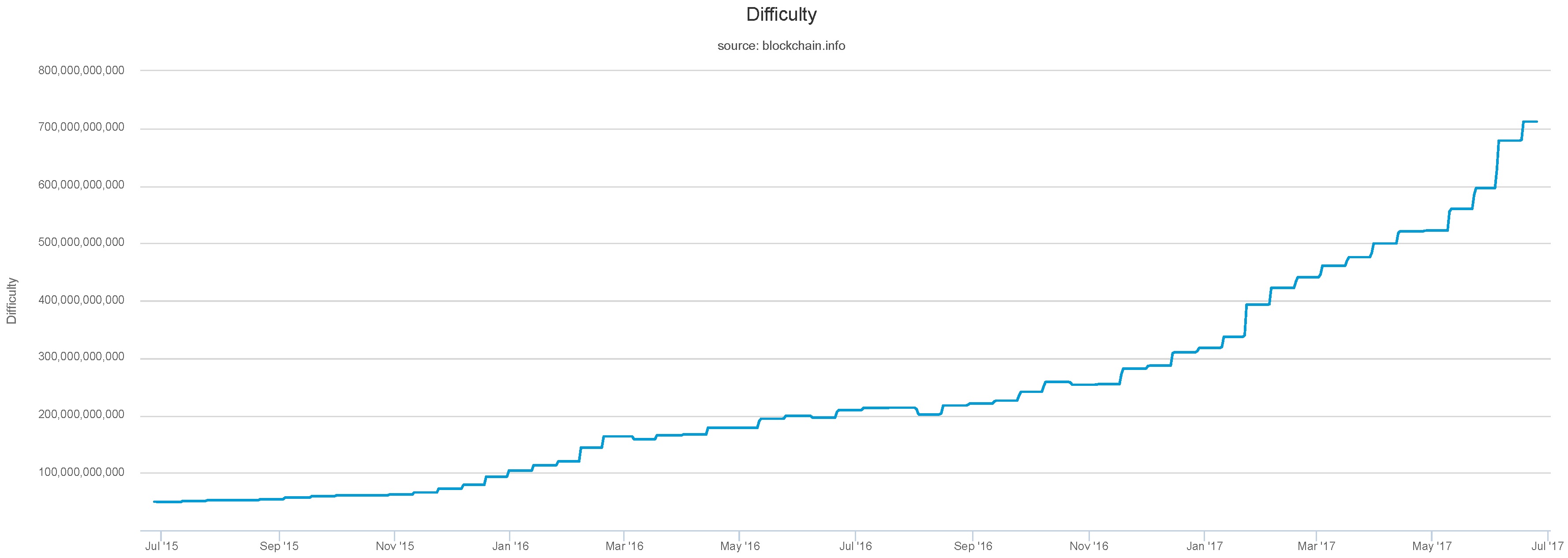
A signature from the root tree is used to sign the public key of the tree below it which signs the tree below it and so on. But why not just go ahead and implement it now and rather than wait until the NSA springs a surprise on us? Consider some very rough estimates: The block chain is currently at ripemd160 bitcoin minerals Had Bitcoin employed either of these signature schemes from the beginning, it would be over gigabytes right now.
Also, note the insane keygen time for GMSS. I suspect, however, that an ASIC hardware wallet would significantly improve that performance. Bitcoin has too many disadvantages to be a tool of the intelligence community.
It is so insecure that it is easily stolen. But there maybe other improvements ripemd160 bitcoin minerals the future ripemd160 bitcoin minerals today no ripemd160 bitcoin minerals can think of — if not today, or not today in 50 years, then in years or years and so. You publish the hash as your address. After this you can repeat the whole thing, just commit to a message that reveals the new codeword, has the new ripemd160 bitcoin minerals of choice and that commits to ripemd160 bitcoin minerals new codeword, wait, then publish the new message.
Now you have a secure and computationally efficient but temporally inefficient signature scheme. Also, this site seems to have a list of every academic paper on post-quantum cryptography ever written. It seems to me though, that since hash functions are already heavily used and scrutinized, the hash-based systems are probably more ready for prime time than the others. Fawkes is pretty ingenious, ripemd160 bitcoin minerals now that you have the block chain.
I was under the impression that the public keys and signatures were ripemd160 bitcoin minerals, around bytes, and more than most hash-based signatures. But looking at it again, it bits. The security seems questionable, however. The paper below is from and it talks about an attack against signatures that allow private key recovery after as little as signatures.
But it does offer up a possible solution and calls for more research.