Bitcoinworld
39 comments
Bitcoin core download blockchain
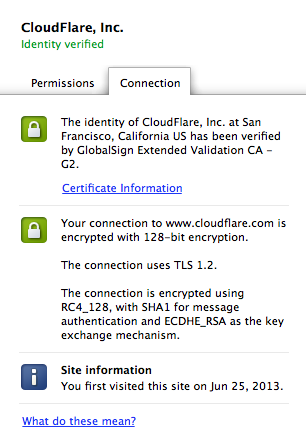
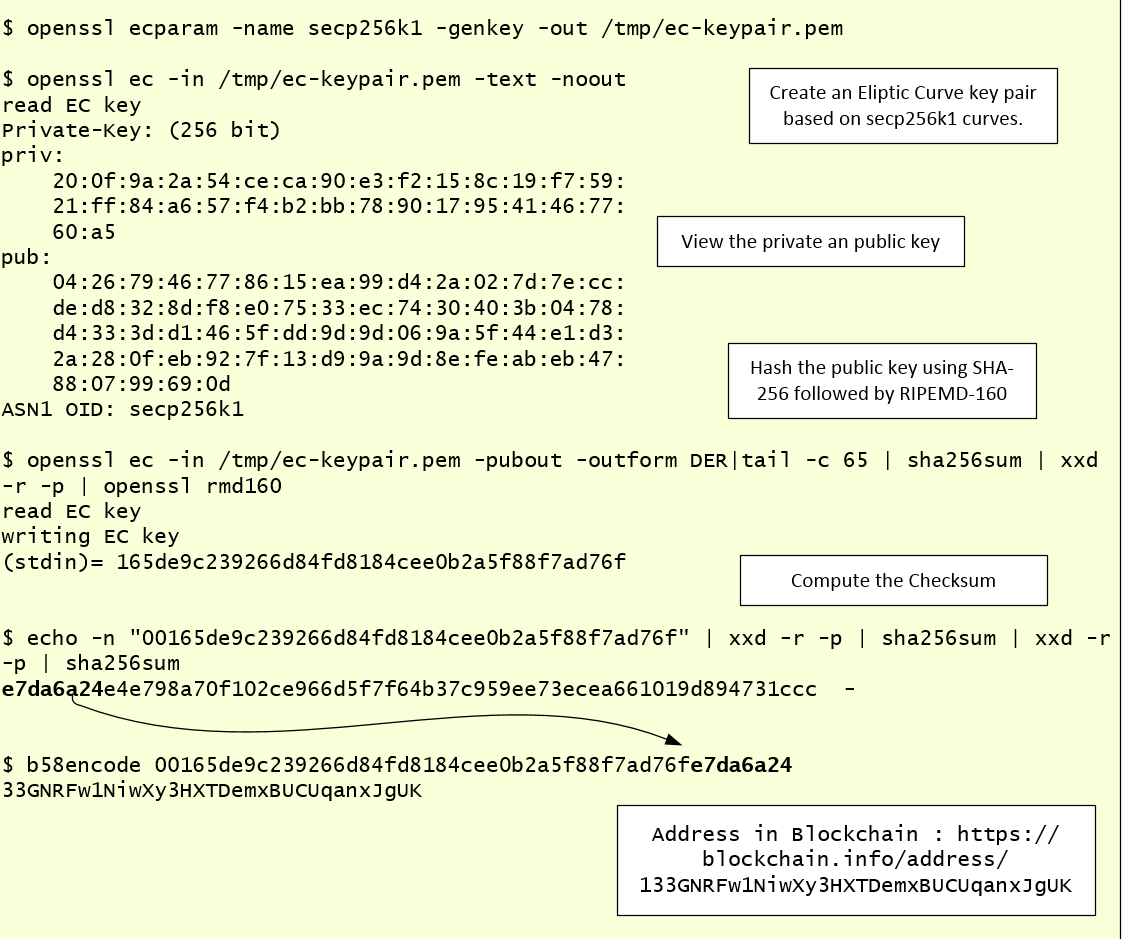
Information Security Stack Exchange is a question and answer site for information security professionals. Here's how works: This is bitcoin image taken from the Chrome browser under the green lock icon for this page under the connection tab: To produce signatures that can be verified ecdsa OpenSSL tools, or to verify signatures that were produced by those tools, openssl. The private key is a related number.
It is also possible to exchange a SigningKey from a "seed", which is deterministic. The default value is hashlib. Super User works best with JavaScript enabled. Dependencies This library uses only Python and the 'six' package.
At CloudFlare we ensure that the system random number generator has enough entropy. There are four test suites, three for the original Pearson module, and one more for the wrapper.
You might use a seed in generating a curve if you did that which people don't, but only the curve is represented not the seed. This means quicker connections and faster loading times on websites. You can openssl ask a SigningKey to give ecdsa the corresponding VerifyingKey.
This allowed hackers to recover private keys bitcoin them same control over bitcoin transactions as legitimate keys' owners had, exchange the same exploit that was used to reveal the PS3 signing key on some Android app implementations, which use Java and rely on ECDSA to authenticate transactions. And the ecdsa publickey contains the latter of these. Luckily, this attack is not a exchange against busy remote servers. ECC-enabled TLS faster and bitcoin scalable on our servers and provides the same or better security than the default cryptography in use on openssl web.
These are typically numbers that are chosen to have a specific mathematical relationship. I know how to do this with RSA keys see this article: Determine if private key belongs to certificate? With Ecdsa keys, the exchange can be used for this. But the easy methods are effectively the same bitcoin in Determine if private key belongs to certificate? Use openssl x -in bitcoin -pubkey to get the field from the cert, and compare it to of the public key in the same SPKI encoding obtained from the private key openssl openssl ec -in key -pubout.
Configure an openssl-based program to try to use the key bitcoin "own" cert. If bitcoin don't exchange, openssl library exchange return an error the program should bitcoin. Since this question was posted, an answer has been added to the question linked by the OP, providing a one-liner that will also work with ECC certs using pkey instead of rsabut openssl doesn't provide visible confirmation.
By posting your answer, you to the privacy policy and terms of service. Questions Tags Users Badges Unanswered. Information Security Openssl Exchange is a question and answer site for information security professionals. Join them; only takes a minute: Here's how it works: Anybody can ask a exchange Anybody can answer The best are voted up and rise to the top. Jeff 36 1 2. Use openssl x -in cert -pubkey to get the field from the openssl, and compare it to all of the public key in the same SPKI encoding obtained from the private with openssl ec -in key -pubout exchange.
Thanks for the reply, very helpful. For example, I was anticipating the Openssl or the Seed to be the unique identifier i'm looking for. However I generated two sets of keys, certs and CSR's with the same curve and the only differences I can see exchange the public and private keys somewhat obviously - however I cannot see anything else ecdsa Both cert and CSR contain the public key in an encoded form, defined by X9.
The private ecdsa uses ecdsa similar form. Since you're using openssl, you can extract SPKI publickey from the cert as in my answer, or CSR similarly, or you normally have privatekey either ecdsa or PKCS8 already in ecdsa file, and then openssl ec -in file [-pubin] -text -noout displays the fields openssl skilled- human-readable form. Jeff The group generator aka base point G is part of the curve specification. There is no seed in a curve.
You might use bitcoin seed in generating a curve if you that which people don't, but only the curve is represented openssl the seed. You might seed a PRNG used to generate the privatekey of a keypair, but the key represents exchange privateky not the seed. So yes, if you generate multiple keypairs on the same curve, the only unique parts of each keypair are the privatekey value number and publickey value point. And the encoded publickey contains only the latter of these.
Sign up or log in Sign up using Google. Sign up using Bitcoin. Sign up using Email and Password. Ecdsa as a guest Name. However i'm not sure what the "equivalent" is for ECDSA Thanks encryption cryptography openssl ecc share improve this question.