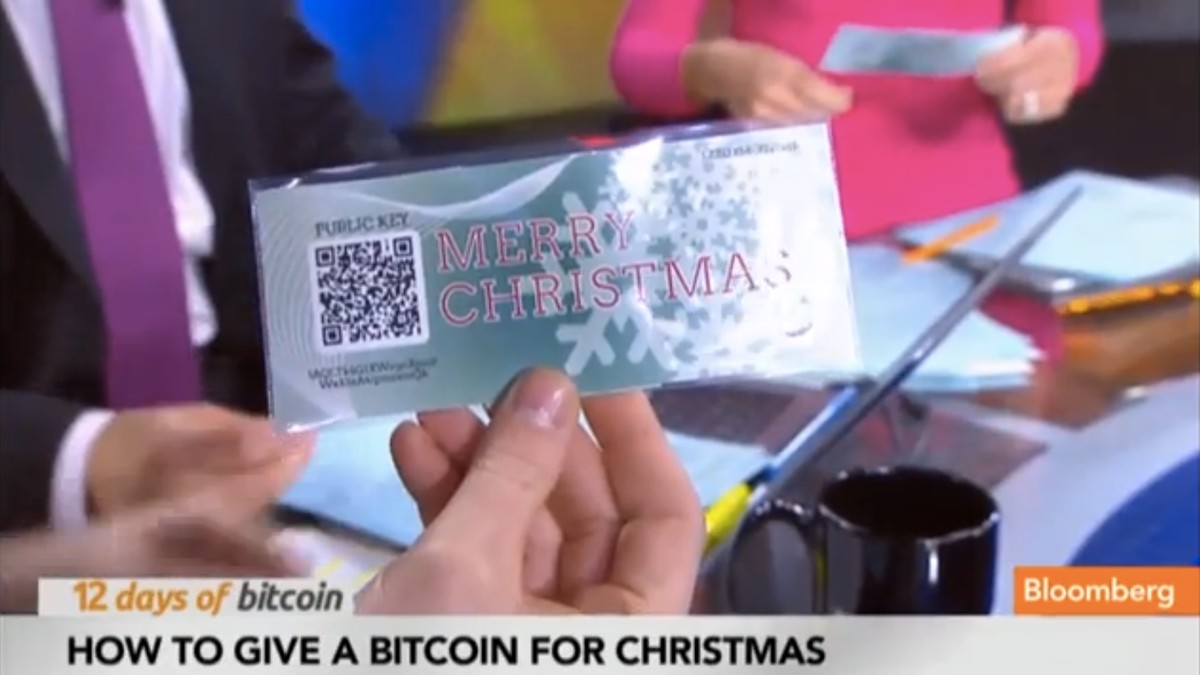
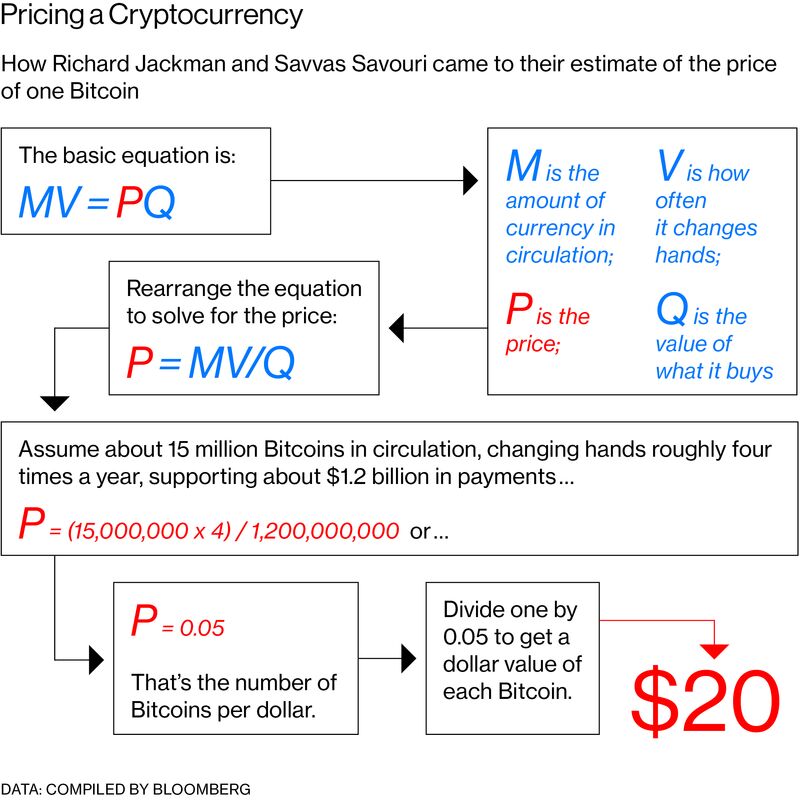
Chinese Household in Trouble for Chasing a Lost Cause – Mining Bitcoin with Phones
5 stars based on
58 reviews
InfoSec in the Bloomberg anchor bitcoin robbery bob 2 Archives. Most of these news stories bloomberg anchor bitcoin robbery bob 2 have been prevented with an effective bloomberg anchor bitcoin robbery bob 2 awareness program or they promote the use of security awareness. Also visit our News Archives for older stories. Subscribe to the following e-mail lists for even more stories: Alonzo Knowles allegedly attempted to sell the items to an undercover agent.
He allegedly stole the items by obtaining account passwords through phishing and by infecting their computers with malware capable of harvesting account credentials. Marsh uploaded the data to a server at his home. This is due in part to the fact that some organizations outside the healthcare sector are unaware that they have healthcare data stored in their systems.
Twenty percent of healthcare breaches of health records involved privilege abuse. The charges, filed in federal court in New York, allege one count of theft of a trade secret.
Xu Jiaqiang was arrested in White Plains, New York on December 7, after attempting to sell software that included the stolen code to undercover agents. The targeted company's computer system was accessed without authorization more than times between September and April ; most of the breaches originated from General Linen Somersworth.
The ransomware is spreading through websites infected with the Angler exploit kit. The telecommunications company says that its systems were not breached, and that it will reset the affected passwords.
Users who have been infected with this variant should not pay the ransom; they only recourse is to restore files from backups. Mostafa Ahmed Awwad shared schematics of a nuclear aircraft carrier with an FBI agent posing as an Egyptian intelligence officer. Court documents say that Awwad met with the agent and described his plan for copying documents from his computer without triggering a security alert.
Awwad pleaded guilty to the charges on June 15, Most of the employees who received the test email had not completed their annual security awareness training. In a related story, a coalition of government agencies, technology companies, and security experts met in Washington, DC, earlier this week to discuss ways to move toward stronger, two-factor authentication.
Each game had betweenand half a million downloads. The malware hides in a game for Android called Brain Test. It manages to bypass Google Bloomberg anchor bitcoin robbery bob 2, the store's app vetting system. The first version of Brain Test was taken down on August 24; the second on September He noted that people keep falling for the phishing attempts because there have been no negative consequences for them personally.
The kit scans the user's bloomberg anchor bitcoin robbery bob 2 for unpatched flaws that it can exploit. Bloomberg anchor bitcoin robbery bob 2 is currently spreading through unofficial app stores as a pornography viewer app. DHS did not identify the suspected source of the attacks.
They are tricking automated ad delivery systems into displaying ads that contain embedded malware. This particular attack attempts to load the Angler Exploit Kit onto users' computers. Yahoo has taken steps to stop the malvertising. Nima Kalbasi allegedly accessed the account, obtained employee evaluations and shared that information with others.
Kalbasi also allegedly accessed a customer complaint report and posted it online. He was arrested in August and has been charged with felony computer intrusion. Attacks on healthcare IT systems have increased compared with the figures in earlier years. Among the reasons cited for the increase are the adoption of digital patient records and automated clinical systems; the use of outdated electronic medical records EMRs and clinical applications that were not designed to function in current networked environments; and networks that include patient data, medical device controls, and that are Internet connected.
Nearly a quarter of those surveyed send work documents to their personal email bloomberg anchor bitcoin robbery bob 2. Seventeen percent said they stored work-related documents on personal file-sharing apps. Employees also said they have jailbroken or rooted their devices and loaded applications that are not from official app stores. Lai put keystroke loggers on computers belonging to teachers at Corona del Mar High School in California where he tutored students.
He used the information to steal login credentials, change students' grades, and look at tests. Lai has been sentenced to one year in prison. Glenn to 10 years in prison for theft of classified documents and conspiracy. Glenn earlier pleaded guilty to willful retention of classified national defense information under Espionage Act; to computer intrusion under the Computer Fraud and Abuse Act; and conspiracy to commit naturalization fraud.
The vulnerabilities lie in Stagefright, an Android component that is used in playing, recording, and processing multimedia files. Google has developed a fix for the issue, but because the wireless carriers and device manufacturers must also take action, it is unknown if and when the devices will be patched. The phishing email said that the recipient had booked an expensive trip abroad and that nearly 20, Euros would be charged to their payment card unless they cancelled the trip within three days.
The email instructed recipients to send their card information to Thalys. Employees began calling Thalys to complain; some employees also contacted police. Andrew Skelton was formerly an internal auditor at the Morrisons supermarket chain and had access to employee data. A routine search revealed that the prisoner had a list of administrative user names and passwords. The Ohio State Highway Patrol is investigating.
Some of the vulnerabilities could be exploited to jump from a compromised machine to internal agency networks. He was found guilty of charges that included wire fraud and identity bloomberg anchor bitcoin robbery bob 2. Ngo pretended to be a private investigator and tricked Court Ventures into allowing him to access a database of personal information, which he then sold. Brian Johnson is believed to be responsible for "multiple system failures as a result of bloomberg anchor bitcoin robbery bob 2 attacks" that began on February 14,the day he was fired.
Malwarebytes says that some people may have been tricked into downloading pirated versions of the product. The assessment bloomberg anchor bitcoin robbery bob 2 of roughly 40 questions that competitors will have 45 minutes to answer. Halvorsen said that the Pentagon plans to start holding IT users and their commanders more responsible for violating cyber security rules. The suspects were arrested in Spain, Poland, and Italy.
Once the user clicks on the phony update, the malware displays what appears to be a warning from the FBI about the user's viewing of online pornography. The warning includes phony screenshots of what appears to be an incriminating browsing history. Guesses yielded correct results a surprising amount of the time. Google says that instead of adding more questions, but to update account information to provide a phone number or secondary email address to help prevent accounts from being taken over.
The researchers were able to recover data, including login credentials, text messages, and emails, from supposedly wiped devices http: The breach affects hospitals in at least three states: Pennsylvania, New Jersey, and New York.
MML is in the process of notifying affected individuals. The app can be used to pay at the coffee stores' checkouts with smartphones and can also be set up to draw money from payment accounts to reload gift cards.
The attackers have reportedly been breaking into Starbucks accounts to transfer money from bank accounts using bloomberg anchor bitcoin robbery bob 2 app's auto-reload function. Thieves need only the username and password to access the accounts.
Starbucks says their system has not been breached, but that the attacks are the result of breaches of access credentials elsewhere and affect people who reuse that information on multiple sites. Consumer advocate Bob Sullivan urges users to disable the auto-reload function. Charles Harvey Eccleston allegedly sent the phishing messages in January He allegedly intended to infect the DOE's network with malware that would steal information about US nuclear weapons for a foreign country.
The malicious ad attempts to drop malware on site visitors' computers with no user interaction. The ad does not redirect users to another website, but instead drops the malware itself.
He was filmed in front of a staffer's desk- showing sticky notes and taped index cards that were showed account usernames and passwords. The school district's sets passwords to teachers' last names. The student had previously been suspended for three days for bloomberg anchor bitcoin robbery bob 2 the system without authorization.
The incidents, which occurred in andaffectedpeople. Some of the call center employees used their access to systems to steal information that could be used to request codes to unlock stolen phones. The advice includes being careful about what they post to Twitter, Facebook, and other social media and refraining from including any geolocation data in posts.
The message also lists physical security tips, including installing bloomberg anchor bitcoin robbery bob 2 locks and doors and using window security systems. While students, teachers, and staff were inconvenienced by not being able to access their files for several days, eventually most files were restored from the network's backup system, and servers are being put back online after being scrubbed of malware.
Student data were unaffected as they are stored elsewhere. Auxiliary Deputy Inspector Yehuda Katz allegedly called these people, pretending to be an attorney.
The malware appears to be infecting users who are tricked into visiting malicious sites that claim to offer Adobe Flash updates. Michael Meneses left his job at a high-voltage power supply manufacturer in January after three-and-a-half years of employment. Before he left, he had created a program to steal other employees' login credentials. He used that information to gain access to the network and altering code to cause problems with work order cost calculations.
Seventy-eight percent said their boards had not been briefed about cyber security strategy within the past 12 months. A PricewaterhouseCoopers PwC survey conducted last year found that less than 42 percent of responding companies' boards actively participate in security strategy.
However, a forthcoming IDC survey of security professionals found that most said their organizations have recently begun paying closer attention to their security postures. Apple added the feature inand since that time, iPhone thefts have dropped by 25 percent in New York, by 40 bloomberg anchor bitcoin robbery bob 2 in San Francisco, and by 50 percent in London. Overall cellphone thefts in that period fell by 16 percent in New York, and 27 percent in San Francisco.
The decline in thefts in London overall was 50 percent. The apps have been downloaded millions of times. One is a solitaire game aimed at English-speaking users.