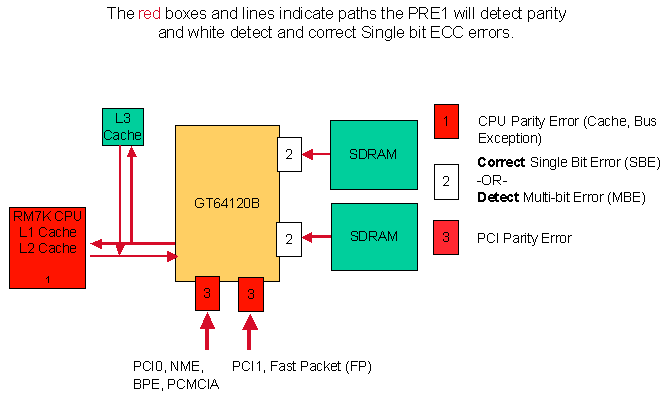
Birthday quotes for big brother in marathi
36 comments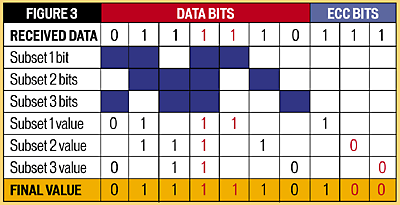
Geometry dash robot gamemode
In telecommunication , Hamming codes are a family of linear error-correcting codes. Hamming codes can detect up to two-bit errors or correct one-bit errors without detection of uncorrected errors. By contrast, the simple parity code cannot correct errors, and can detect only an odd number of bits in error. Hamming codes are perfect codes , that is, they achieve the highest possible rate for codes with their block length and minimum distance of three.
In his original paper, Hamming elaborated his general idea, but specifically focused on the Hamming 7,4 code which adds three parity bits to four bits of data. In mathematical terms, Hamming codes are a class of binary linear codes. The parity-check matrix of a Hamming code is constructed by listing all columns of length r that are non-zero, which means that the dual code of the Hamming code is the shortened Hadamard code.
The parity-check matrix has the property that any two columns are pairwise linearly independent. Due to the limited redundancy that Hamming codes add to the data, they can only detect and correct errors when the error rate is low. This is the case in computer memory ECC memory , where bit errors are extremely rare and Hamming codes are widely used. In this context, an extended Hamming code having one extra parity bit is often used.
Extended Hamming codes achieve a Hamming distance of four, which allows the decoder to distinguish between when at most one one-bit error occurs and when any two-bit errors occur. Richard Hamming, the inventor of Hamming codes, worked at Bell Labs in the s on the Bell Model V computer, an electromechanical relay-based machine with cycle times in seconds.
Input was fed in on punched paper tape , seven-eighths of an inch wide which had up to six holes per row. During weekdays, when errors in the relays were detected, the machine would stop and flash lights so that the operators could correct the problem. During after-hours periods and on weekends, when there were no operators, the machine simply moved on to the next job. Hamming worked on weekends, and grew increasingly frustrated with having to restart his programs from scratch due to detected errors.
In a taped interview Hamming said, "And so I said, 'Damn it, if the machine can detect an error, why can't it locate the position of the error and correct it? In , he published what is now known as Hamming Code, which remains in use today in applications such as ECC memory. A number of simple error-detecting codes were used before Hamming codes, but none were as effective as Hamming codes in the same overhead of space.
Parity adds a single bit that indicates whether the number of ones bit-positions with values of one in the preceding data was even or odd. If an odd number of bits is changed in transmission, the message will change parity and the error can be detected at this point; however, the bit that changed may have been the parity bit itself.
The most common convention is that a parity value of one indicates that there is an odd number of ones in the data, and a parity value of zero indicates that there is an even number of ones. If the number of bits changed is even, the check bit will be valid and the error will not be detected. Moreover, parity does not indicate which bit contained the error, even when it can detect it.
The data must be discarded entirely and re-transmitted from scratch. On a noisy transmission medium, a successful transmission could take a long time or may never occur. However, while the quality of parity checking is poor, since it uses only a single bit, this method results in the least overhead. A two-out-of-five code is an encoding scheme which uses five bits consisting of exactly three 0s and two 1s. This provides ten possible combinations, enough to represent the digits 0—9.
This scheme can detect all single bit-errors, all odd numbered bit-errors and some even numbered bit-errors for example the flipping of both 1-bits. However it still cannot correct any of these errors. Another code in use at the time repeated every data bit multiple times in order to ensure that it was sent correctly.
If the three bits received are not identical, an error occurred during transmission. If the channel is clean enough, most of the time only one bit will change in each triple. Therefore, , , and each correspond to a 0 bit, while , , and correspond to a 1 bit, with the greater quantity of digits that are the same '0' or a '1' indicating what the data bit should be. Such codes cannot correctly repair all errors, however. In our example, if the channel flips two bits and the receiver gets , the system will detect the error, but conclude that the original bit is 0, which is incorrect.
If we increase the size of the bit string to four, we can detect all two-bit errors but cannot correct them, the quantity of parity bits is even at five bits, we can correct all two-bit errors, but not all three-bit errors. Moreover, increasing the size of the parity bit string is inefficient, reducing throughput by three times in our original case, and the efficiency drops drastically as we increase the number of times each bit is duplicated in order to detect and correct more errors.
If more error-correcting bits are included with a message, and if those bits can be arranged such that different incorrect bits produce different error results, then bad bits could be identified. In a seven-bit message, there are seven possible single bit errors, so three error control bits could potentially specify not only that an error occurred but also which bit caused the error.
Hamming studied the existing coding schemes, including two-of-five, and generalized their concepts. To start with, he developed a nomenclature to describe the system, including the number of data bits and error-correction bits in a block. For instance, parity includes a single bit for any data word, so assuming ASCII words with seven bits, Hamming described this as an 8,7 code, with eight bits in total, of which seven are data.
The repetition example would be 3,1 , following the same logic. Hamming also noticed the problems with flipping two or more bits, and described this as the "distance" it is now called the Hamming distance , after him. Parity has a distance of 2, so one bit flip can be detected, but not corrected and any two bit flips will be invisible. The 3,1 repetition has a distance of 3, as three bits need to be flipped in the same triple to obtain another code word with no visible errors.
It can correct one-bit errors or detect but not correct two-bit errors. A 4,1 repetition each bit is repeated four times has a distance of 4, so flipping three bits can be detected, but not corrected. When three bits flip in the same group there can be situations where attempting to correct will produce the wrong code word.
Hamming was interested in two problems at once: During the s he developed several encoding schemes that were dramatic improvements on existing codes. The key to all of his systems was to have the parity bits overlap, such that they managed to check each other as well as the data.
The following general algorithm generates a single-error correcting SEC code for any number of bits. The form of the parity is irrelevant. Even parity is mathematically simpler, but there is no difference in practice. Shown are only 20 encoded bits 5 parity, 15 data but the pattern continues indefinitely.
The key thing about Hamming Codes that can be seen from visual inspection is that any given bit is included in a unique set of parity bits. To check for errors, check all of the parity bits. The pattern of errors, called the error syndrome , identifies the bit in error.
If all parity bits are correct, there is no error. Otherwise, the sum of the positions of the erroneous parity bits identifies the erroneous bit. If only one parity bit indicates an error, the parity bit itself is in error.
As m varies, we get all the possible Hamming codes:. If, in addition, an overall parity bit bit 0 is included, the code can detect but not correct any two-bit error, making a SECDED code.
The overall parity indicates whether the total number of errors is even or odd. If the basic Hamming code detects an error, but the overall parity says that there are an even number of errors, an uncorrectable 2-bit error has occurred. Hamming codes have a minimum distance of 3, which means that the decoder can detect and correct a single error, but it cannot distinguish a double bit error of some codeword from a single bit error of a different codeword.
Thus, some double-bit errors will be incorrectly decoded as if they were single bit errors and therefore go undetected, unless no correction is attempted. To remedy this shortcoming, Hamming codes can be extended by an extra parity bit. Thus the decoder can detect and correct a single error and at the same time detect but not correct a double error. If the decoder does not attempt to correct errors, it can detect up to three errors.
This extended Hamming code is popular in computer memory systems, where it is known as SECDED abbreviated from single error correction, double error detection. Particularly popular is the 72,64 code, a truncated , Hamming code plus an additional parity bit, which has the same space overhead as a 9,8 parity code. In , Hamming introduced the [7,4] Hamming code. It encodes four data bits into seven bits by adding three parity bits. It can detect and correct single-bit errors. With the addition of an overall parity bit, it can also detect but not correct double-bit errors.
This is the construction of G and H in standard or systematic form. Regardless of form, G and H for linear block codes must satisfy. The parity-check matrix H of a Hamming code is constructed by listing all columns of length m that are pair-wise independent.
Thus H is a matrix whose left side is all of the nonzero n-tuples where order of the n-tuples in the columns of matrix does not matter. So G can be obtained from H by taking the transpose of the left hand side of H with the identity k- identity matrix on the left hand side of G.
Finally, these matrices can be mutated into equivalent non-systematic codes by the following operations: The [7,4] Hamming code can easily be extended to an [8,4] code by adding an extra parity bit on top of the 7,4 encoded word see Hamming 7,4.
This can be summed up with the revised matrices:. Note that H is not in standard form. To obtain G, elementary row operations can be used to obtain an equivalent matrix to H in systematic form:. For example, the first row in this matrix is the sum of the second and third rows of H in non-systematic form.
Using the systematic construction for Hamming codes from above, the matrix A is apparent and the systematic form of G is written as. The non-systematic form of G can be row reduced using elementary row operations to match this matrix. The addition of the fourth row effectively computes the sum of all the codeword bits data and parity as the fourth parity bit. For example, is encoded using the non-systematic form of G at the start of this section into 01 1 0 0 where blue digits are data; red digits are parity bits from the [7,4] Hamming code; and the green digit is the parity bit added by the [8,4] code.
The green digit makes the parity of the [7,4] codewords even. Finally, it can be shown that the minimum distance has increased from 3, in the [7,4] code, to 4 in the [8,4] code. Therefore, the code can be defined as [8,4] Hamming code. From Wikipedia, the free encyclopedia.