Cex exchange astoria
36 comments
Auto binary trading bot
Why Linux over Windows? If you missed the hardware portion of our guide, make sure to check it out first. You should end up in the BIOS configuration area. Xubuntu is a lightweight version of Ubuntu, a popular Linux distribution. That should bring up a remote terminal session to your miner, which is more or less just like sitting at the keyboard in front of it.
Make sure that you use a strong Xubuntu password! I highly recommend that you complete the remainder of the guide in this manner, as it eliminates the risk of typos! The final command will reboot your rig, which will cause you to immediately lose your SSH Putty connection. Wait a few seconds to give the computer a chance to boot, and then re-establish a new connection via Putty, and re-login. Remember your password, and keep multiple backups of your key file s!
The author abandoned development months ago, so improvements are unlikely. You should see the Claymore miner start up. We want to set up our rigs automatically start mining whenever the rig is powered on. Creating an alias will make that easy. The easiest way to do that is to close your Putty session and power down your miner. Turn it back on and the following should happen:. I used this guide a while back, then decided to go back to Windows.
Windows crashed hard and never gave me better hash rates, so back to Ubuntu! Thanks so much for this guide and thanks for keeping it current! I followed your guide step by step and all is well except for when I start the miner I get this error:. DRM version is 2. I had error message related to libOpenCL. In nanopool, I want to change min payout to 0. Hey EP, I have the same issue. Lightdm was causing some issues. The latest available version of Ubuntu on their website I theorize instilling an old version of Ubuntu If you change the version to match yours it will downgrade but not far enough.
And trying to many times may break your OS. I currently have kernel version 4. I have applied the FAQ instruction previously. Checked my version according to your instruction and mine is also 4. Looks like the slowdown is not a result of the version? Any help will be appreciated. When i tryo yo check my account on eth. I get an account not found. Even after i have over share. Thanks for the great instruction.
Unfortunately i have some problems. Everything works great for a day sometimes longer. It is not enough to deinstall the gpu driver. I use 5 x R9 with two W power supplies. Do you have any idears. Thanks for this walk through worked amazingly well with the nvidia rig. Tried reinstalling the drivers and swapping the kernel version to 4. Are there any links that will detail the GPU optimization for ubuntu? Strap the cards in windows environment up, then put them back into your ubuntu rig.
Hello, I believe this would work for me if I could just get the right download. Maybe consider updating to the latest Claymore Miner version Thanks for your great work. I followed your instructions after January reboot with subsequent dropped hashrate. Everything was back to normal and my machine set not to update automatically.
Today I rebooted again, hashrate per card went down from to System responded by telling me nothing removed since it is not installed. Is there another procedure to follow now to get the hashrate up again?
I followed all steps until reach step 7 and try to run the miner using claymore Ver Finaly, after crawling through countless poorly written, hard to follow posts and more youtube videos than I care to admit this one did the trick.
I just got my modest rig hashing for the first time on ubuntu the way I had imagined and hoped it would. Segmentation fault core dumped. Notify me of follow-up comments by email. Notify me of new posts by email. Build your own Ethereum Mining Rig, part 2: Change power options so that the computer automatically turns itself on whenever power is restored. The reason for this is two-fold: Exact tweaks vary by motherboard, but setting the PCIe speed to Gen1 is usually a good place to start.
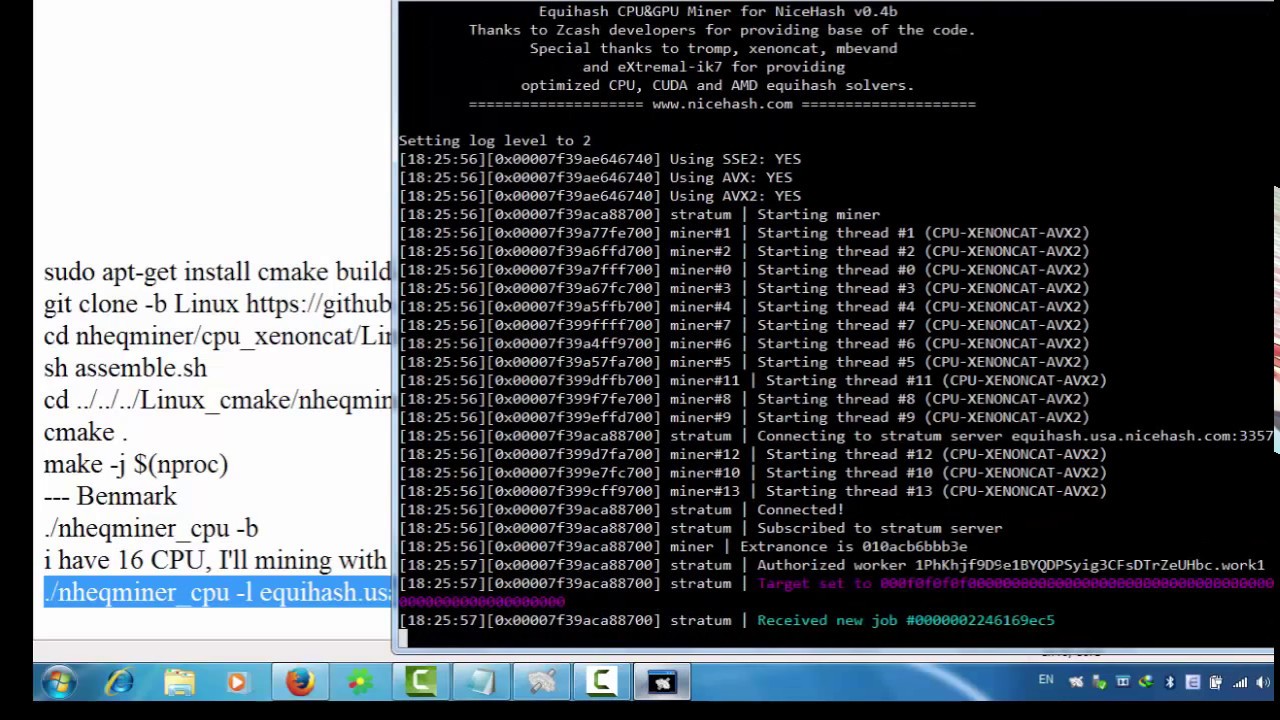
Install Xubuntu Desktop on your miner Xubuntu is a lightweight version of Ubuntu, a popular Linux distribution. You can download it here. The Xubuntu installer should appear. When the installation is complete, you should automatically boot into the Xubuntu desktop. Make sure to remove your installation media. Install SSH by typing: When the installation is complete, type the following: Type the following to open your grub file in nano for editing: Type the following to install the necessary ethereum packages: Note that commands below just clean up the installation directory a bit by removing an intermediary directory that was included in the original tar archive: You can fire up your miner by typing: Turn it back on and the following should happen: Your miner should boot into Xubuntu.
Linux Setup RoscoeP says: February 7, at February 8, at February 20, at February 25, at 5: April 4, at 9: February 8, at 3: February 10, at February 27, at 5: February 14, at 1: February 16, at 7: The Mining King says: February 18, at April 22, at 4: February 20, at 3: February 25, at 1: March 8, at 9: March 10, at 5: March 14, at 1: April 24, at 9: May 4, at 9: