Liliana monero
32 comments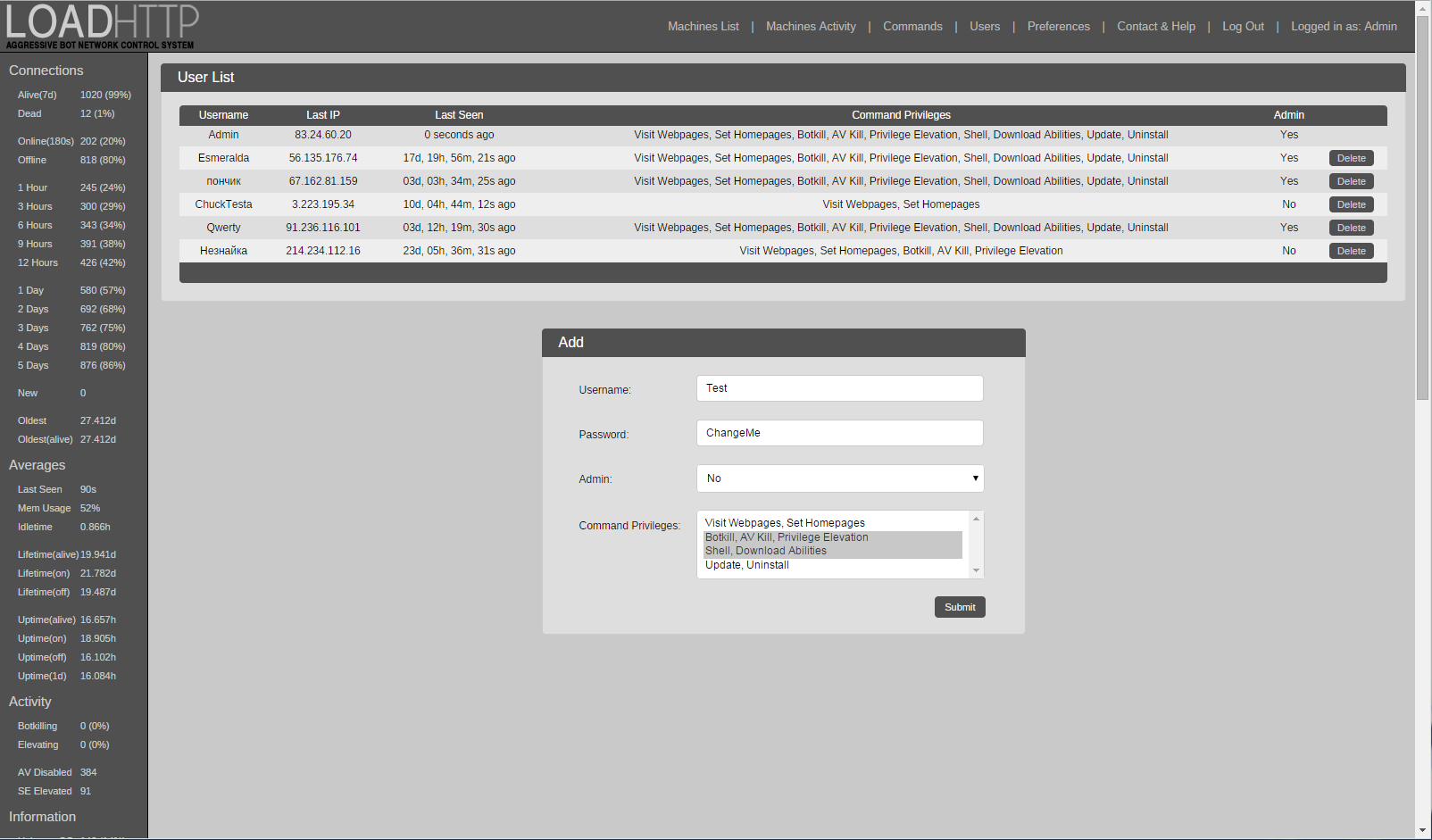
Bitcoin qt testnet wallet inserts
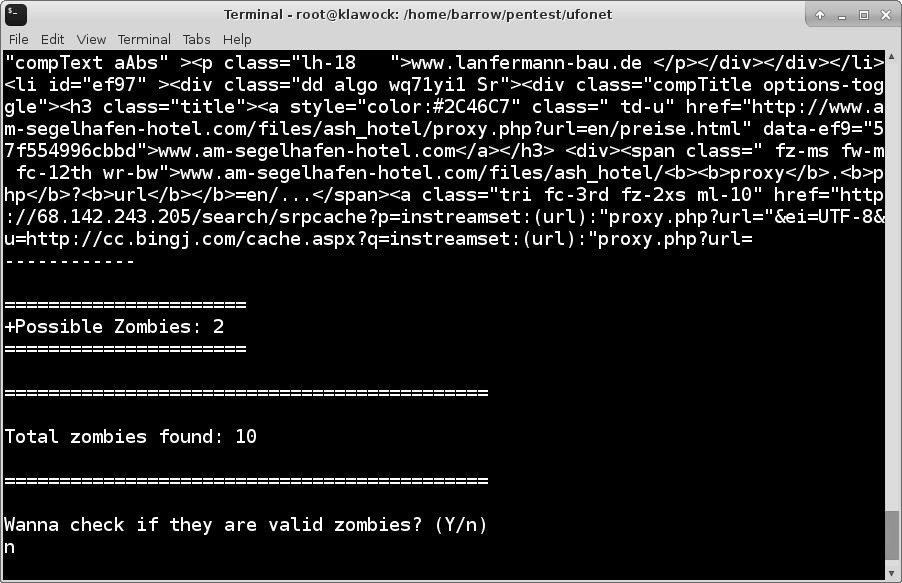
Cryptocurrency mining is an IT industry buzzword and a rapidly growing phenomenon. In doing so, these miners come up with more and more ingenious ways, not all of which are legal, to earn the coveted coins. We have written before about botnets and how hackers can turn your computer into a zombie and make it a part of a botnet.
A network of such zombie computers can be used for a variety of purposes, including but not limited to cryptocurrency mining. Several thousand computers on a botnet can mine cryptocurrencies much more effectively than a single computer can. In the case of a mining botnet, victims also foot the electricity bill, making installing miner applications on the computers of unsuspecting users a very lucrative business for hackers. Note that a rank-and-file user can install a miner application intentionally, to mine cryptocurrency on their own.
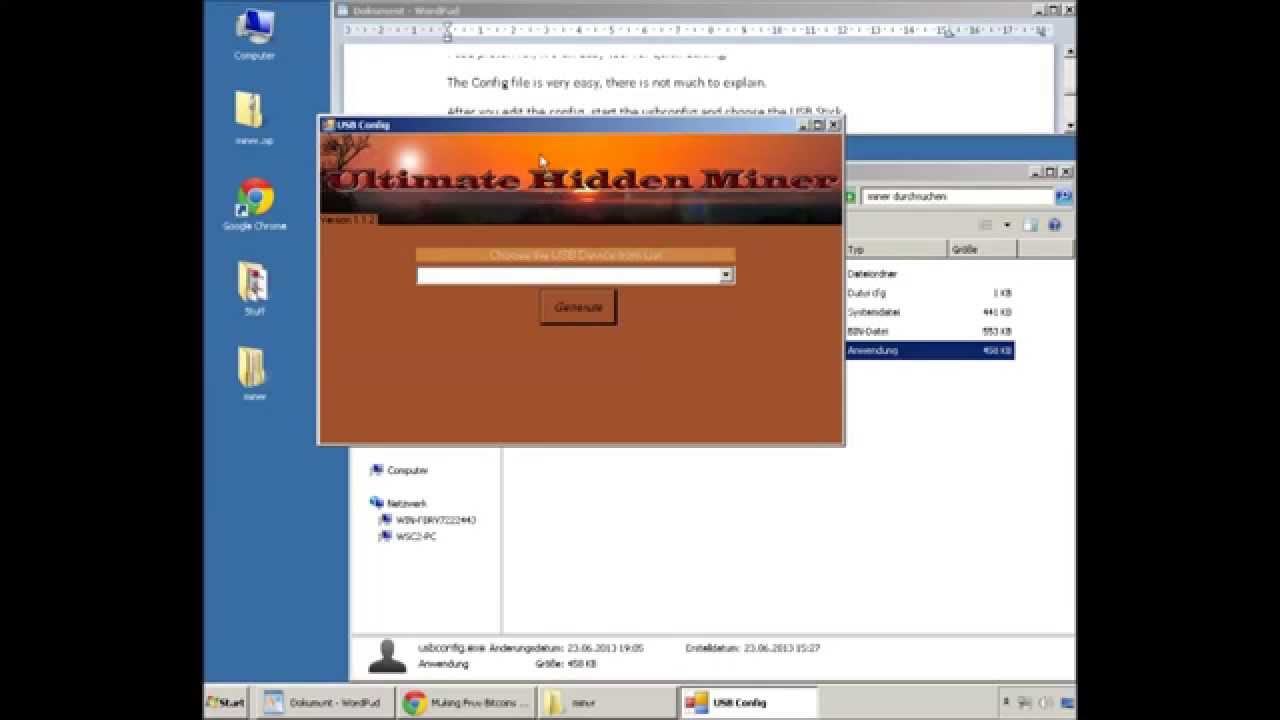
Distinguishing legal mining from illegal activity is the challenge. Miner applications are identical; the difference is in the covert installation and operation of illegally acting applications. In most cases, a miner ends up on a computer with the help of a purpose-built malicious application, a so-called dropper whose chief function is to secretly install another application. Droppers usually come under the guise of pirated versions of licensed products or activation key generators for them.
Users look for this type of software on peer-to-peer networks and download it intentionally. The application can also come complete with services that ensure its autorun and configure its settings. For example, such services can suspend the miner when the user starts certain popular computer games. Such services can also attempt to disable antivirus products, suspend the miner when a system monitoring tool is running, and restore the miner if the user tries to delete it.
Hackers distribute such applications as a service. They use Telegram channels devoted to online work opportunities; you might come across ads offering trial versions of such droppers for distributing a hidden miner.
To give you an idea of the scale of this phenomenon: Our experts recently detected a botnet consisting of an estimated several thousand computers on which the Minergate miner was secretly installed. It mines not highly popular bitcoins but mostly those cryptocurrencies, such as Monero XMR and Zcash ZEC , that allow the concealing of transactions and wallet ownership. Monero wallet, used by criminals, mentioned above. Kaspersky Internet Security protects you against malicious droppers by default.
If for some reason you deactivate AV and run a manual scan after becoming suspicious, Kaspersky Internet Security will immediately detect this full-fledged Trojan and prompt you to get rid of it.
Unlike droppers, miners are not malicious applications, as we mentioned earlier. Kaspersky Internet Security does not block or remove such applications by default; a user may have installed them on purpose. Last but not least, scan your system regularly: Your security solution will help you avoid installing and running any unwanted applications.
Different types of SSL certificates. Are your devices hurting your relationship? The battle for e-privacy. Yaroslava Ryabova 20 posts. Got any hidden miners? Why miners need your computer We have written before about botnets and how hackers can turn your computer into a zombie and make it a part of a botnet. How a hidden miner ends up on your computer In most cases, a miner ends up on a computer with the help of a purpose-built malicious application, a so-called dropper whose chief function is to secretly install another application.
Scale of the problem Hackers distribute such applications as a service. Transatlantic Cable Podcast, Episode 2. How to avoid Android malware. Different types of SSL certificates Quiz: Don't show me this message again.
Products to Protect You Our innovative products help to give you the Power to Protect what matters most to you. Discover more about our award-winning security. In just a few clicks, you can get a FREE trial of one of our products — so you can put our technologies through their paces.