Bitcoin europe price
23 comments
Cex io wallet
It offers free updates and lets you immunise your Internet browser against future infection by known malware. The spyware and malware protection for computers running Microsoft Windows is a very important issue. There are thousands of new malware being created every day. Attack methods are becoming increasingly sophisticated. The preventive measures outlined in the previous paragraph are mandatory for all computers running Microsoft Windows.
In addition, we strongly recommend the usage of Spybot as described in this chapter. However, if your computer gets infected despite these precautions, and you find yourself requiring additional Microsoft Windows tools, we recommend the following:. It also lets you immunise your system against adware, malware and spyware, preventing them from infecting your computer once Spybot is installed.
It can however run along side anti-virus software to enhance security of your PC. Adware is any software which displays advertising material on your computer. Certain kinds of adware function remarkably like spyware and can be invasive of your privacy and security. Spyware is any kind of program that collects data, observes and records your private information and tracks your Internet habits. Like malware, it frequently runs on your computer secretly. As such, installing a program like Spybot will help you to protect your system and yourself.
Windows Vista, 7 and 8 have a built-in anti-spyware program called Windows Defender. However, it seems to allow Spybot to work without any conflict.
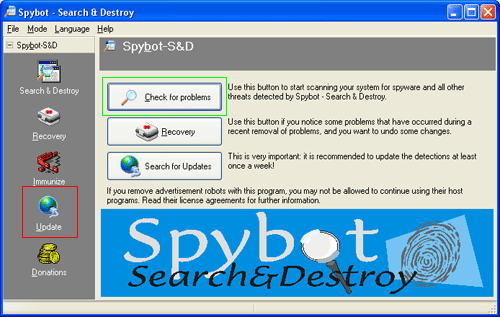
Once Spybot is installed, you can use it to identify and remove spyware by following three basic steps:. For a brief overview of key advanced options, please refer to the Advanced Options section. Double click ; the Open File - Security Warning dialog box may appear.
If it does, click to activate the following screen:. Click at the Donations Welcome screen choosing the default option I am installing Spybot for personal use, and will decide later. Click at the Installation and Usage Mode screen choosing the default option I want to be protected without having to attend it myself. Click at the License Agreement screen.
Please read the License Agreement before proceeding with the rest of the installation process. Click at the Ready to Install screen to begin the installation:. By default, the Check for new malware signatures is selected as shown above. Note - If an Internet connection is not available during the install, untick this box and review the Section 2.
Click to activate the screen below. After you have completed the installation and set-up process, Spybot will automatically launch itself to the Start Center. Before you begin, it is strongly advised that you create a backup of the registry. For an overview of the Windows Registry , please refer to CCleaner for more information.
Click in the Startup Tools window. Select a location and file name as shown in figure 10 below at the Folder to save to window. It is absolutely vital that you keep Spybot up to date with the latest definitions. The automated update feature is not available in the free version of Spybot so you must run this updated manually following the steps below:. Click in the Start Center to activate the Updater ;. Click to activate as shown below:. Spybot helps shield your computer from known spyware by "immunising" it.
This is like receiving a vaccination against infectious new diseases. Click from the Start Center to activate the Immunization window below:. If you have left your browser open for some reason, the following screen will appear before you begin the immunisation process:. Click to begin checking for immunized files if you have not yet immunized your system, few or no immunized files will be found:. Click to begin immunising your system.
Immunization make take several minutes to run. Click Show Details to view detail as shown below:. You can reverse or undo the immunisation process if you suspect that immunising your system has negatively affected the overall performance of your computer.
You may click to reverse the immunisation process and restore your system to its previous state. Before you begin checking for potential threats, please run the Spybot Updater.
Click to launch the Spybot Start Center. Click to activate the screen below:. Click to begin scanning your system. Note - If you have a lot of data, files, programmes etc. After the scan has been completed, the number and kinds of potential malware found will be listed as shown below:. Select the file and review the Details box on the left of the screen for each potential threat found to determine if the malware is a genuine threat.
Remember - a false positive means that a harmless file, folder, program or registry key could be categorised as malware. Deleting such could cause an issue an issue to another program. The Threat Level is displayed by a colour indicator bar. As the Threat Level moves from Medium to High , the colour indicator will change from orange to red. At a glance, it will be easy to gauge the potential threat.
For example, most Browsers used Tracking Cookies when you visit a website. If the information they store is not excessive, the Estimated Danger rating my be Marginal or Very Low.
You may choose to keep the cookies for certain websites for convenience. If you choose to delete a file or files select the file and click. You can also choose to to scan individual files and folders using the File Scan option in the Start Center - the process is similar to the System Scan described above.
A tracking Cookie is a small file saved on your computer by an Internet browser when you visit a website. A cookie can store information that can identify you to a particular website. This can include information such as username, password, personal data used to fill online forms, browsing habits etc. While Cookies provide convenience when browsing, this poses a risk to your anonymity online. Click to launch the following screen:.
Click to display the browser profiles on your computer as shown below. Note - there may be other browser profiles on your computer. Select the profile and click:. To re-enable Tracking Cookies , click on the drop-down arrow beside and select. The Quarantine tool allows you to recover or retrieve any previously deleted or repaired item. This is possible because Spybot will create a backup for every item it has previously deleted.
If a deleted file causes your computer to malfunction, it is possible to restore it using the Quarantine tool. Click from the Start Center to launch the screen below:. Check the items you would like to recover from the list of previously deleted items, and then click. Alternatively, click to remove checked files completely. However, be aware that purged items are not recoverable. Spybot has Default and Advanced sections. The Advanced Mode lets you configure settings and perform additional tasks.
The free version of Spybot only allows you to use some of the options available in the Advanced Tools and Professional Tools sections:. Report Creator can be used to assist Spybot Technical Support teams in the event that you need help with Spybot software. The level of support available will usually depend on the version of software you are running - paid verse free for example.
While support forums are a useful source of knowledge to help decide if a file is harmful or not, we do recommend caution before submitting any files or logs from your computer if anonymity is a concern for you. Startup Tools section lets you review in details processes active on your computer, programs that are run when your computer is starting, your system scheduled tasks, plugins, system services, installed programs, etc..
Rootkit Scan section checks your computer operating system for presence of rootkits , malicious programs that hide at the system level, which makes them undetectable by standard anti-malware tools. The Rootkit Scan can be used to flag suspicious files and registry entries for further analysis or for removing them. The steps below will show how to perform a Rootkit Scan. Click from the Advanced Tools pane to activate the window below.
Note Quick scan test results. Select the drives and registry entries you wish to scan. We recommend selecting all of the items available. Note this scan can take long time perhaps about an hour to complete. When the scan has completed, Search for rootkits will display any suspicious files found. You can then review the findings and options to determine if the file is legitimate. Select Scan file for malware if this option is available. This will activate the File Scan window.