Lojas online que aceitam bitcoin charts
21 comments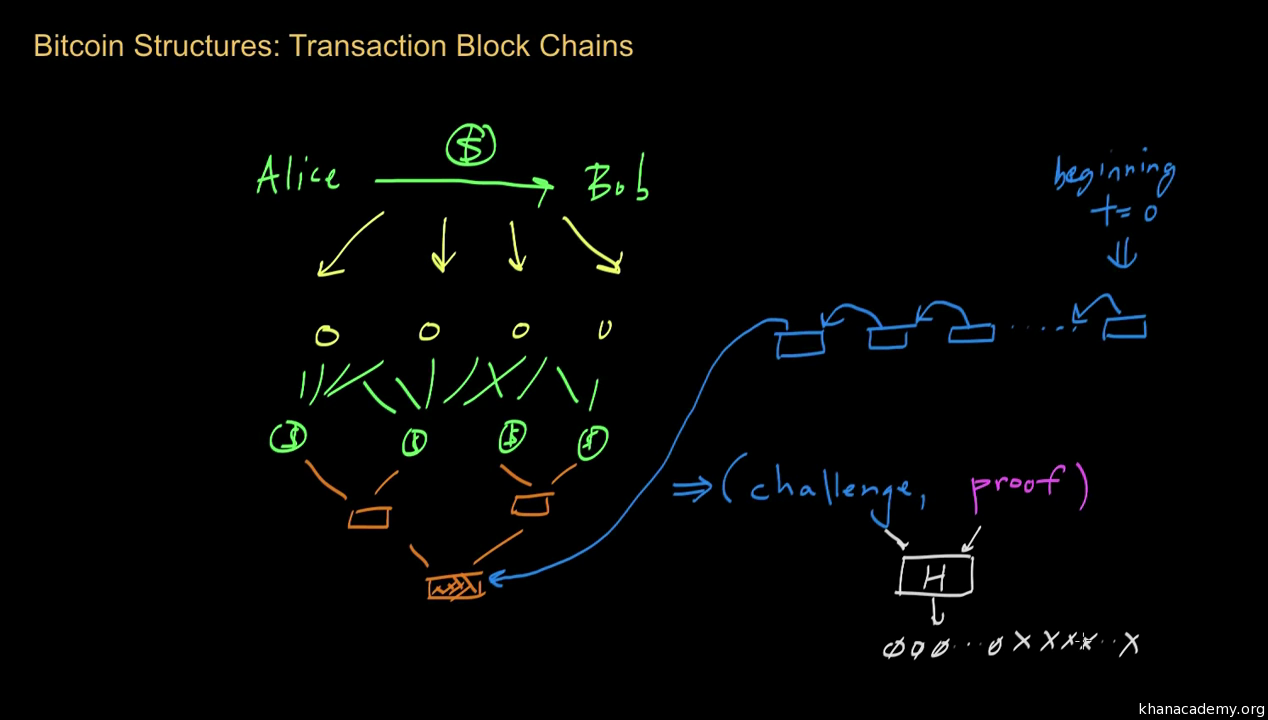
Tener monedero bitcoin
Beyond its role as a protocol for managing and transferring money, the Bitcoin protocol creates a complex system of economic incentives that govern its inner workings. These incentives strongly impact the protocol's capabilities and security guarantees, and the path of its future development. This article explores these economic undercurrents, their strengths and flaws, and how they influence the protocol.
Bitcoin, which continues to enjoy growing popularity, is built upon an open P2P peer-to-peer network of nodes. Key to Bitcoin's security is its resilience to manipulations by attackers who may choose to join the system under multiple false identities.
After all, anyone can download the open-source code for a Bitcoin node and add as many computers to this network as they like, without having to identify themselves to others. To counter this, the protocol requires nodes that participate in the system to show proof that they exerted computational effort to solve hard cryptographic puzzles proof-of-work in order to participate actively in the protocol.
Nodes that engage in such work are called miners. The system rewards miners with bitcoins for generating proof-of-work, and thus sets the incentives for such investment of efforts.
The first and most obvious effect of participants getting paid in bitcoins for running software on their computers was that, once bitcoins had sufficient value, people started mining quite a lot. In fact, efforts to mine intensified to such a degree that most mining quickly transitioned to dedicated computer farms that used specialized gear for this purpose: The Bitcoin network quickly grew and became more secure, and competition for the payments given out periodically by the protocol became fierce.
Before discussing the interplay between Bitcoin's security and its economics, let's quickly look at the rules of the protocol itself; these give birth to this complex interplay.
Users who hold bitcoins and wish to transfer them send transaction messages via software installed on their computer or smartphone to one of the nodes on the Bitcoin network. Active nodes collect such transactions from users and spread them out to their peers in the network, each node informing other nodes it is connected to about the requested transfer.
Transactions are then aggregated in batches called blocks. Blocks, in turn, are chained together to create the blockchain , a record of all accepted bitcoin transactions. Each block in the chain references its predecessor block by including a cryptographic hash of that block—effectively a unique identifier of that predecessor.
A complete copy of the blockchain is kept at every node in the Bitcoin network. The process of block creation is called mining. One of its outcomes among others is the printing of fresh coins, which we call minting.
The rules of the protocol make block creation extremely difficult; a block is considered legal only if it contains the answer to a hard cryptographic puzzle. As compensation, whenever miners manage to create blocks they are rewarded with bitcoins. Their reward is partly made up of newly minted bitcoins and partly of mining fees collected from all of the transactions embedded in their blocks.
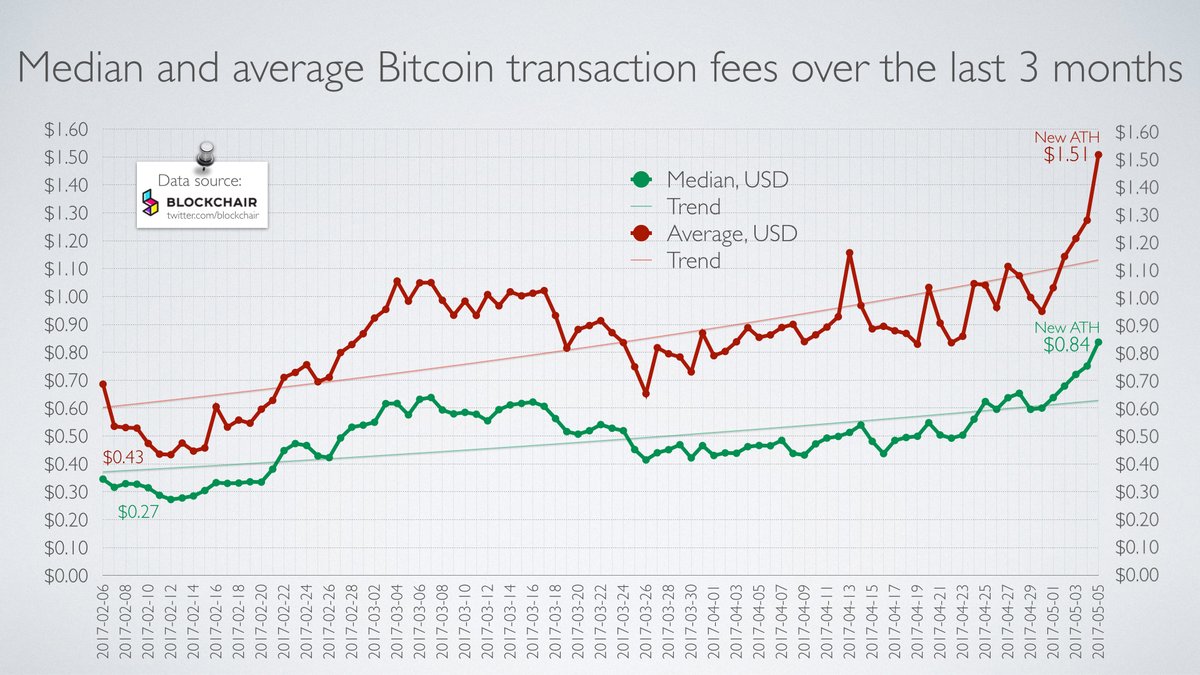
The rate of minting is currently This amount is halved approximately every four years. As this amount decreases, Bitcoin begins to rely more and more on transaction fees to pay the miners. The key to Bitcoin's operation is to get all nodes to agree on the contents of the blockchain, which serves as the record of all transfers in the system. Blocks are thus propagated quickly to all nodes in the network. Still, it is sometimes possible for nodes to receive two different versions of the blockchain.
For example, if two nodes manage to create a block at the same time, they may hold two different extensions to the blockchain. These blocks might contain different sets of payments, and so a decision must be made on which version to accept. The Bitcoin protocol dictates that nodes accept only the longest chain as the correct version of events, as shown in figure 1. To be more precise, nodes select the chain that contains the most accumulated computational work.
This is usually the longest chain. This rule, often called the "longest chain rule," provides Bitcoin with its security. An attacker who wishes to dupe nodes into believing that a different set of payments has occurred will need to produce a longer chain than that of the rest of the network—a task that is incredibly difficult because of the proof-of-work required for each block's creation. In fact, as long as the attacker has less computational power than the entire Bitcoin network put together, blocks and transactions in the blockchain become increasingly harder to replace as the chain above them grows.
This difficulty in replacing the chain implies that it takes many attempts before an attacker can succeed in doing so. These failed attempts supposedly impose a cost on attackers—mining blocks off of the longest chain without getting the associated mining rewards. Figure 1 shows the evolution of the blockchain: Blocks that are off the longest chain are eventually abandoned.
They are no longer extended, their contents transactions colored in red are ignored, and the miners that created them receive no reward. At point 1 there are two alternative chains resulting from the creation of a block that did not reference the latest tip of the blockchain.
At point 2 the fork is resolved, as one chain is longer than the other. At point 3 there is another fork that lasted longer, and at point 4 the second fork is resolved.
Bitcoin's rate of block creation is kept roughly constant by the protocol: The difficulty of the proof-of-work required to generate blocks increases automatically if blocks are created too quickly. This mechanism has been put in place to ensure that blocks do not flood nodes as more computational power is added to the system. The system thus provides payments to miners at a relatively constant rate, regardless of the amount of computational power invested in mining.
Clearly, as the value in U. More participants then find it profitable to join the group of miners, and, as a consequence, the difficulty of block creation increases. With this increase in difficulty, mining blocks slowly becomes more expensive. In the ideal case, the system reaches equilibrium when the cost of block creation equals the amount of extracted rewards. In fact, mining will always be slightly profitable—mining is risky, and also requires an initial investment in equipment, and some surplus in the rewards must compensate for this.
Hence, Bitcoin's security effectively adjusts itself to match its value: As mining rewards continue to decline as per the protocol's mining schedule , the incentive to create blocks is expected to rely more on transaction fees. If a sudden drop in bitcoin transaction volume occurs, these fees might be insufficient to compensate miners for their computational resources.
Some miners might then halt their block creation process, temporarily. This may compromise the system, as the security of transactions depends on all honest miners actively participating. For additional work on the incentives in Bitcoin after mining declines, see Carlsten et al.
Many complain that the computation required to create blocks wastes resources especially electricity and has no economic goal other than imposing large costs on would-be attackers of the system. The proof-of-work is indeed a solution to a useless cryptographic puzzle—except, of course, that this "useless" work secures the Bitcoin network.
But what if some of the work could be useful? Or could be produced more efficiently? If mining does not entail a waste of resources for each node, then it also costs nothing for attackers to attack the system. In fact, if the proof-of-work is less costly to solve, more honest participants join mining to collect the rewards , and soon the difficulty adjustment mechanism raises the difficulty again.
Hence, in a sense, the Bitcoin proof-of-work is built to spend a certain amount of resources no matter how efficient an individual miner becomes. To derive substantial benefits from mining without an offsetting increase in costs requires a proof-of-work that is useful to society at large but cannot provide value to the individual miner.
For some attempts at using other problems as a basis for proof-of-work, see Ball et al. The key aspect of the Bitcoin protocol is its decentralization: This promotes both the resilience of the system, which does not have a single anchor of trust or single point of failure, and competition among the different participants for mining fees. To maintain this decentralization, it is important that mining activity in Bitcoin be done by many small entities and that no single miner significantly outweigh the others.
Ideally, the rewards that are given to miners should reflect the amount of effort they put in: In practice, some participants can benefit disproportionately from mining, for several different reasons. An unbalanced reward allocation of this sort creates a bias in favor of larger miners with more computational power, making them more profitable than their smaller counterparts and creating a constant economic undercurrent toward the centralization of the system.
Even slight advantages can endanger the system, as the miner can use additional returns to purchase more and more computational power, raising the difficulty of mining as the miner grows and pushing the other smaller and, hence, less profitable miners out of the game. The resulting winner-takes-all dynamic inevitably leads to centralization within the system, which is then at the mercy of the prevailing miner, and no security properties can be guaranteed.
ASICs were orders of magnitude more efficient at mining bitcoins than previous systems. As this special hardware was not initially easy to acquire, it provided its owners with a great advantage over other miners—they could mine at a much lower cost.
Those with this advantage would add ASIC-based proof-of-work to the system until the difficulty level would be so high that everyone else would quit mining. The risk was then that a single large miner would have sole access to ASICs and would come to dominate the Bitcoin system. Concerns subsided after some time, as ASICs became commercially available and more widely distributed.
In fact, ASIC mining actually introduces long-term effects that contribute to security. Later this article looks at how a miner can carry out profitable double spending and selfish mining attacks. One can argue, however, that even selfish and strategic miners are better off avoiding such attacks. Indeed, a miner who invested millions of dollars in mining equipment such as ASICs is heavily invested in the future value of Bitcoin: Should the miner then use this gear to attack the system, confidence in the currency would drop, and with it the value of bitcoins and future rewards.
The interests of miners are thus, in some sense, aligned with the overall health of the system. All in all, ASIC mining introduces a barrier-to-entry to the system, as ordinary people cannot simply join the mining efforts; it thus reduces decentralization. On the other hand, it introduces a form of barrier-to-exit , as miners cannot repurpose their equipment to other economic activities; it therefore contributes to security. The appearance of competing cryptocurrencies e. This introduces complex market dynamics.
For example, when a specific currency loses some value, miners will divert their mining power to another cryptocurrency until the difficulty readjusts. This can cause fluctuations in block creation that destabilize smaller cryptocurrencies. Interestingly, some cryptocurrencies use different proof-of-work puzzles that are thought to be more resistant to ASIC mining, i.
This is often achieved by designing algorithmic problems that require heavy access to other resources, such as memory, and that can be solved efficiently by commercially available hardware.
These alternative systems are in principle more decentralized, but on the flip side they lack the barrier-to-exit effect and its contribution to security. A similar effect occurs when cloud mining becomes highly available.