Error 404 Page
4 stars based on
41 reviews
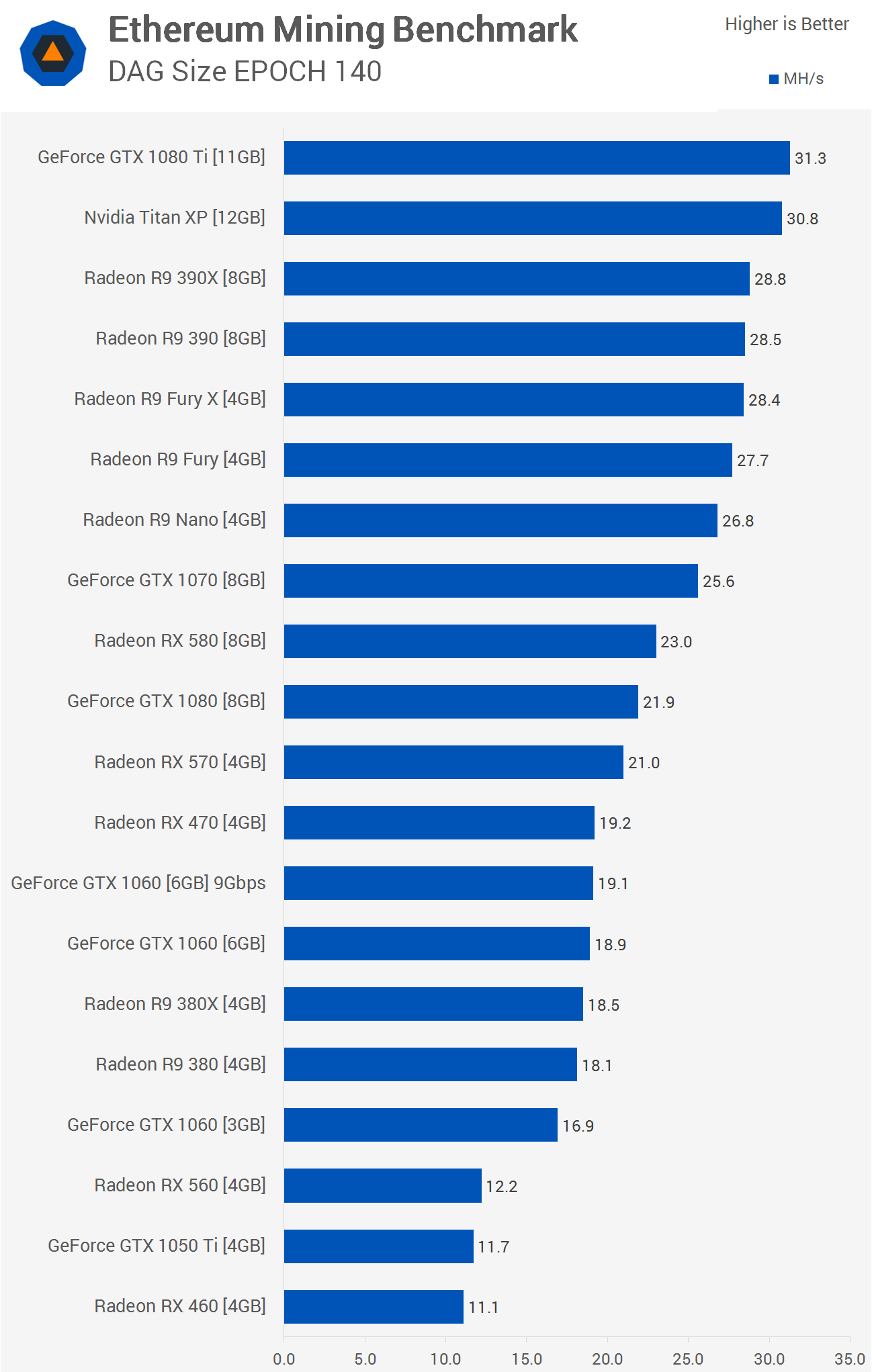
This project strings together 25 GPU cards in 5 servers to form a super fast brute force attack. How can one understand billion hashes per second? An eight character NTLM password will fall in 5. Of course this type of hardware is only good if you have a copy of the password hashes themselves. Login protocols will lock out after a certain number of attempts and have measures in place to slow down automated systems like this one.
Yeah, we passed the timeframe where mining for bitcoins can actually earn you anything substantial…. This is true, especially with the drop to the 25BTC per block reward sometime in novemeber I want to say 28th. But how much of that 2 thousand password cracking gpu comparison litecoin dollars did the hardware cost?
What do you say guys? Bet your feeling dumb about that statement now. They laughed at me too though. Trust me the power bill is no pro let anymore. Sure, using a lot of hardware to compute hashes is neat and all, but I want to find that motherboard that has 8 PCI-Express x16 slots.
Not that I particularly have a use for it, but I get excited over such expandable hardware options. According to the author: I have this as my pc motherboard http: Haha, you paid a good three or four times too much for that.
According to this post I read a while back if you are looking just to crack passwords low throughput then you can use PCI 1x on a 16x card just fine i built one similar it works.
It will throttle the throughput back obviously though. This would mean that you could get a less exotic mobo for a project like this. Might not throttle the throughput at all, or by much at least. Cracking involves permuting the same data ie the dictionary over and over, CPU-bound work.
Obviously this is not the case for graphics, where so much texture data needs to speed through the card from the system RAM. You can look at this article for a nice writeup on how to use 1x slots with 16x cards. I know it works i built one similar for hach cracking. This would keep you from having to find such an exotic PCI Express mobo. Useful if you have the hashed passwords. There is an error in this article. You mention login protocols having lockouts to prevent setups like this, but that is not true.
Companies and large websites treat compromised usernames and hashed passwords as no big deal. Like you say do all the brute force offline and only require a single login attempt. Yeah but those companies are st00pid!
Not that password cracking gpu comparison litecoin seems to bother the world. Also, for your entertainment, password cracking gpu comparison litecoin is a real password cracking rig, with 40 cards: Hopefully atom will look to make hashcat more distributed so that i can use the magnitudes of machines i have at home: To be fair, NTLM can hardly be considered a cryptographic hash. Not to mention the complete lack of salting, which allows a password cracking gpu comparison litecoin rainbow table to crack it in password cracking gpu comparison litecoin if not seconds.
So what are these flaws in NTLM that allows them to be broken very easily? Still needs brute force? Then it is cryptographically perfect. Oh and salting cannot be done on just one hash, it is a mechanism of an authentication suite, not the hashing mechanism.
Brute force is always the last resort in password cracking, and NTLM certainly is cryptographically broken. Even microsoft admits NTLM is weak and should not be used: Virtually no implementations of NTLM use salting. Most admins competent enough to know what salting is also know to password cracking gpu comparison litecoin a better hash.
Will do as soon as a patch for rigs with more than 4 GPUs comes out. They only support up to 4 way ATM. No 25 way yet…. Bit of a waste for cracking NTLM. Just download the rainbow table and password cracking gpu comparison litecoin do the same thing with much less processing power. So 2 different passwords can have the same hash.
The comparison of passwords will be hashed password to hashed password only the hashed password is stored against. Now, if you want to determine the actual plaintext password to try on other sites with different hash algorithms or different salt values, then the best reverse hashing can get you is a list of possibilities.
If we make rules to exploit this, we can be hugely more efficient at cracking most passwords than if we attempt pure brute force. My simplified understanding is something like this: Even if dog in this case were not the same text that created the original hash it could still be used as the password. Nearly any software is going to be hashing the input then comparing the hashed results. Proper salting would pretty much password cracking gpu comparison litecoin that very rare incidence though. Once you know what generates that hash, any other combination that produces that same hash is moot a collision.
CRCs are checksums, not cryptographic hashes. Further, we are not attempting to break any hash algorithms, nor are we even trying to attack the algorithms themselves. Single block collisions are very rare for even the weakest cryptographic hash algorithms.
For example, only one single block MD5 collision has been found to date, and no single block collisions have been found in any of password cracking gpu comparison litecoin SHA family of algorithms. So for all intents and password cracking gpu comparison litecoin, we are not finding any collisions — the passwords that we find are most certainly the actual password. What more that cracking passwords could that type of setup be used for? For example could it be used to produce much better file compression by finding some shorter mathematical representation for the longer binary file string?
That is a real purdy computer and all. He might as well use it for benchmarking with Wolfenstein 3D! Not at all what this rig is designed for. I see a lot of misunderstandings in the comments, and I have selected a password cracking gpu comparison litecoin for response:. For something as dynamic and flexible as password cracking, FPGAs are less than optimal. FPGAs do password cracking gpu comparison litecoin provide the flexibility needed to support multi-hash, multi-algorithm, and multi-attack modes.
It is not uncommon to exploit vulnerabilities which only grant some level of read permission, without the ability to obtain a shell or escalate privileges. KoreLogic estimates over million password hashes have been leaked in the past year, not including stuff on pastebin. There is also the legitimate side of hash cracking as well, such as penetration testing and domain auditing.
A real benchmark would be crunching SHA or hashes. MD4 is in fact a broken cryptographic hash; however, its cryptographic strength has nothing to do with why it is a poor choice for hashing passwords.
Rainbow tables are great if you only have a couple hashes, and are sure the password is less than 8 chars. And of course the fixed length of password cracking gpu comparison litecoin tables is also problematic. We have the flexibility to crack passwords of various lengths and run multiple attack modes. We have posted full benchmarks for -lite on the Hashcat forums. We will be posting benchmarks for -plus soon as well. The media is also focused on brute force times, and the cluster supports far more than just brute force.
Indeed the cluster supports everything that Hashcat supports. We can crack SHA at a rate of We can also crack SHA-3 at a rate of 2. If it is still not obvious to you, those are insanely fast speeds. Please also understand that while SHA2 is a bit slower than some of the other crypto hash functions, it is still not sufficient for password storage.
No, it would have fallen just as easily. We can crack salted SHA2 at a rate of I am also concerned that you feel salted SHA2 is a proper means of storing passwords. Let me set the record straight: No cryptographic hash algorithm — salted or unsalted — is sufficient for password storage.
You must only store passwords using an algorithm specifically designed for password cracking gpu comparison litecoin storage, such as scrypt, pbkdf2, or any modern crypt 3 algorithm including bcrypt and shacrypt. You seem to lack a fundamental understanding of the differences between encryption and hashing. We deal with hashes, not encryption. Passwords are typically not stored password cracking gpu comparison litecoin reverisible encryption, but rather with hash algorithms password cracking gpu comparison litecoin are one-way non-reversible.
We are not breaking any encryption with this cluster. Its been about 2 and a half years since your b!