Liquide vaisselle carrefour drive
39 comments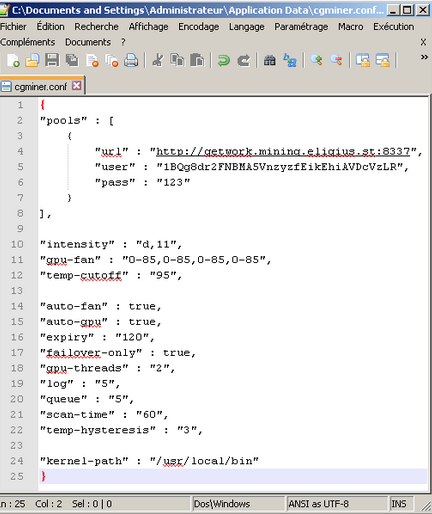
Wladimir j van der laan bitcoin news
Most Internet users are familiar with the concept of updating software that resides on their computers. But this past week has seen alerts about an unusual number of vulnerabilities and attacks against some important and ubiquitous hardware devices, from consumer-grade Internet routers, data storage and home automation products to enterprise-class security solutions. The firewall built into routers can be a useful and hearty first line of protection against online attacks, because its job is to filter out incoming traffic that the user behind the firewall did not initiate.
But things get dicier when users enable remote administration capability on these powerful devices, which is where this malware comes in. In response, Linksys said the worm affects only those devices that have the Remote Management Access feature enabled , and that Linksys ships these products with that feature turned off by default. The Ars Technica story includes more information about how to tell whether your router may be impacted.
Similarly, it appears that some ASUS routers — and any storage devices attached to them — may be exposed to anyone online without the need of login credentials if users have taken advantage of remote access features built into the routers, according to this Ars piece from Feb.
More details on this vulnerability are available at this SecurityFocus writeup. ASUS reportedl y released firmware updates last week to address these bugs. Alternatively, consider dumping the stock router firmware in favor of something more flexible, less buggy amd most likely more secure see this section at the end of this post for more details. Outfitting a home or office with home automation tools that let you control and remotely monitor electronics can quickly turn into a fun and addictive if expensive hobby.
But things get somewhat more interesting when the whole setup is completely exposed to anyone on the Internet. According to research released today, multiple vulnerabilities in these WeMo Home Automation tools give malicious hackers the ability to remotely control the devices over the Internet, perform malicious firmware updates, and access an internal home network.
An increasing number of malware samples in the wild are using host systems to secretly mine bitcoins. Bitcoin is a decentralized, virtual currency, and bitcoins are created by large numbers of CPU-intensive cryptographic calculations. In addition to archiving transactions, each new ledger update creates some newly minted bitcoins.
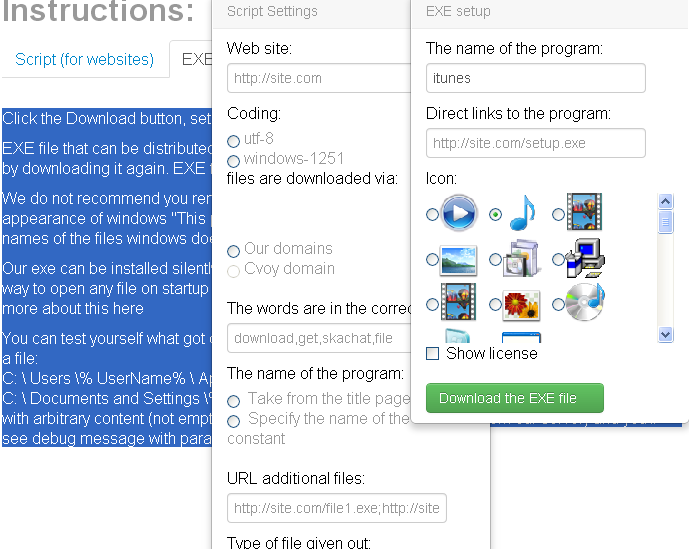
Earlier this week, I learned of a Russian-language affiliate program called FeodalCash which pays its members to distribute a bitcoin mining bot that forces host PCs to process bitcoin transactions hat tip to security researcher Xylitol. Because services like Virustotal share information about new malware samples with all participating antivirus vendors, scanning the installer will make it more likely that antivirus products on host PCs will flag the program as malicious.
Rather, the administrator urged users who want to check the files for antivirus detection to use a criminal friendly service like scan4u[dot]net or chk4me[dot]com, which likewise scan submitted files with dozens of different antivirus tools but block those tools from reporting home about new and unidentified malware variants. This Google-translated version of the site shows the builder for the installer. I gained access to an affiliate account and was able to grab a copy of the mining program.
I promptly submitted the file to Virustotal and found it was flagged as a trojan horse program by at least two antivirus products. This analysis at automated malware scanning site malwr. It also indicates that the program beacons out to pastebin.
Also, the administrator demands that new users demonstrate the ability to garner hundreds to thousands of installs per day. This is a rather high install rate, and it appears many if not all affiliates are installing the mining program by bundling it with other executable programs distributed by so-called pay-per-install PPI programs.
Follow me on Twitter. Join me on Facebook. Krebs on Security In-depth security news and investigation. Bitcoin Mining by Botnet An increasing number of malware samples in the wild are using host systems to secretly mine bitcoins. The FeodalCash bitcoin mining affiliate program. Your email account may be worth far more than you imagine.