Error establishing a database connection
5 stars based on
51 reviews
This raises a whole set of terrible and weird issues for exchanges, casinos and other large-scale hot wallet providers. Also, of course, any participant in Ethereum that might care what happens to their coins in Classic-land, in case Classic ends up being the dominant chain.
I wrote about some attack vectors hereand Dr. ETH classic aint da answer, y'all chillen wit a dead chain playin necromancer, terminal illness, ur chain got cancer.
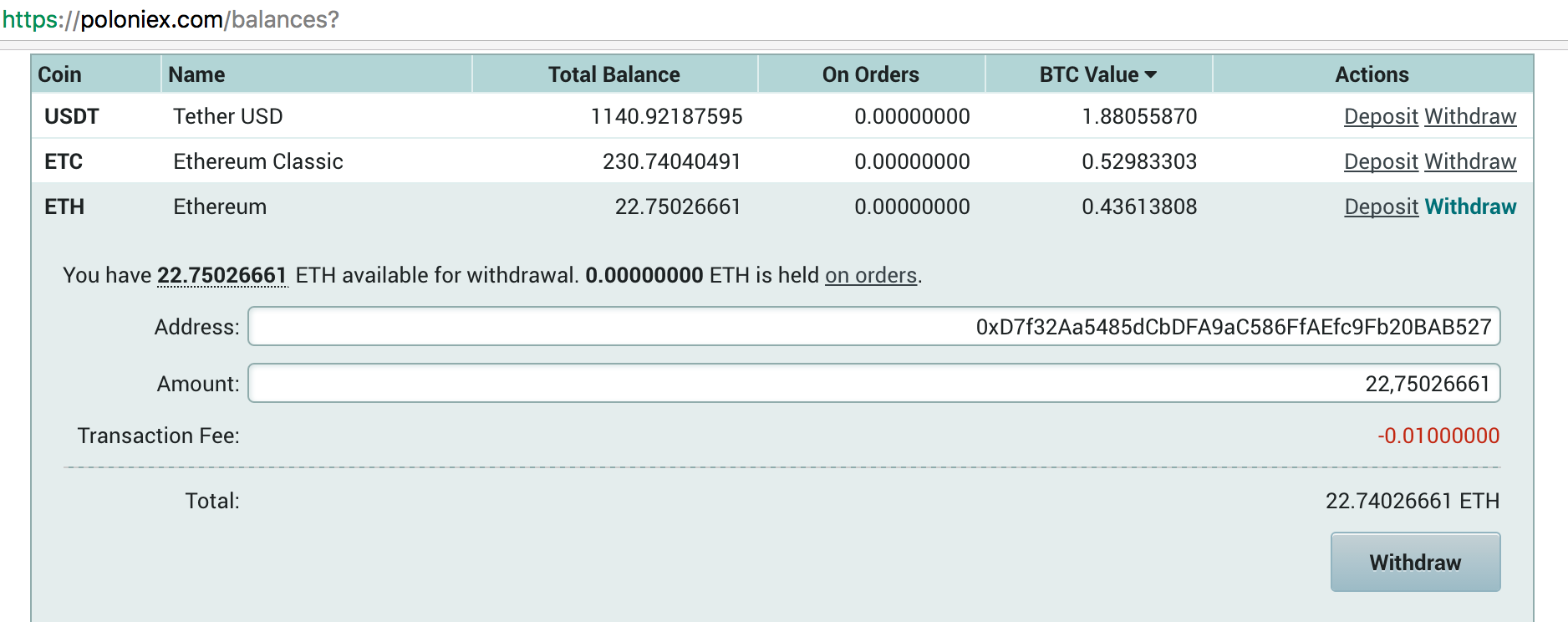
The simplest worry is that you're going to get replayed in one chain, poloniex eth address generating you do something in the other: More complex, and harder to reason about, are worries about multi-contract interactions, calls happening with varying state, all the things that are bread and butter for attackers in distributed systems or complex software. You wish to get a little Bitcoin in exchange for your Classic coins, which you think are worthless. You send them to Poloniex, at their ETC deposit address.
You sell the coins, withdraw Bitcoin, and are happy. Where did they go? Some ETH-Classic supporter has sent them on to the same address as Poloniex' ETH-Classic deposit address, but this time on the main chain, poloniex eth address generating simply replaying the transaction in the main chain.
If you are very, very lucky, Poloniex may be able to keep track of these coins on the main chain for you. But, probably, they are going to be lost until and unless someone can manually see what's going on and help you out. Any contract which relies on ordered state concerns has real trouble coming. Sirer posed to me a simple poloniex eth address generating to get the point across: Imagine a contract takes moves in a TTT game, and implements poloniex eth address generating following rules: A replayer can force a loss on either side in Classic by selectively withholding one side's moves, and double-playing the other's.
The TTT contract will note an illegal move, and give the win to the other side. Or, a game player can get a guaranteed win without a forfeit -- she will know her opponents moves ahead of time, and can interject new moves of her own that lead to a win. Another way of saying this is that most Ethereum contract calls are not idempotent -- they rely on the blockchain to encapsulate enough state to function.
If your mind poloniex eth address generating running through some questions about your own multisig wallets or DAOs in which you control funds or are part of an authorization team, it should be. The answers are not pretty. Because contracts can rely on anythingexisting balances, output from other contracts outside their control, block hashes, you may be in for a pretty bad time.
Let's imagine you have a list of payout addresses in Classic, and one in the main chain. And let's imagine that the main chain contract continues on merrily, while the Classic one poloniex eth address generating, because your DAO has decided to use the main chain.
Now, let's imagine a large payout is made and approved, perhaps an "upgrade" -- moving all funds to a new version of the contract -- using the following set of steps:. This is like the TTT vulnerability above; we replace one 'move' poloniex eth address generating a new one, and the rest of the calls can remain invariant.
There are hundreds of possibilities like this, from casino attacks to exchange attacks. It is going to be insanity, real and true insanity. In my first essay about this, I recommended simultaneously moving your ethereum to different contracts, one per chain.
Since writing up my thoughts, I have learned about a proposal by Tjaden Hess -- a 'many universes' contract which could make this a bit easier. The idea of the many universes contract is to create a number of 'slots', each one owned by a different address. For safety, I would recommend that each of these addresses be generated by a different private key -- in the ideal world, you will put your original wallet's private key on ice, and not use it, except in emergency.
When money comes in, the poloniex eth address generating checks the most recent blockhash, and uses that to choose a slot, sending all money to poloniex eth address generating slot. If the blockhashes differ and they will differ post-forkthen the money will be controlled by different addresses in each universe.
This makes replay attacks on cash difficult. Of course, you might end up in the same slot. Especially if you're going to be hand-coding in the addresses, the question of how many slots are needed is worth considering. This is a variant of the birthday problem. That could be a lot of work. Don't send ether out on the Classic chain for any reason unless you want to be replay attacked; first split your ether into new addresses, one per chain.
Then you can enjoy. If you have more difficult circumstances, e. I and my team are available for consultation around issues like these: It looks like, sadly, ETH classic is a going concern, at least for a little while. Now, though we aren't talking theoretical problems, but real ones.
ETH classic aint da answer, y'all chillen wit a dead chain playin poloniex eth address generating, terminal illness, ur chain got cancer Worries The simplest worry is that you're going to get replayed in one chain, whenever you do something in the other: Selling Coins at Poloniex You wish to get a little Bitcoin in exchange for your Classic coins, which you think are worthless.
Call Authorizations And Mucking With State Any contract which relies on ordered state concerns has real trouble coming. DAO Vulnerabilities Let's imagine you have a list of payout addresses in Classic, and one in the main chain. Now, let's imagine a large payout is made and approved, perhaps an "upgrade" -- moving all funds to a new version of the contract -- using the following set of steps: Address is added to a list of payout proposals Payout proposal is voted on and accepted Payout is made If anyone is allowed to add a payout proposal, then the attack looks like this: Replay txs for the DAO under attack until one before the address being added Add your own address as a proposal Replay additional votes and payout transaction from main chain Boom, you've got control of the poloniex eth address generating.
Mitigation In my first essay about this, I recommended simultaneously moving your ethereum to different contracts, one per chain.
All contracts that can manage to do this should do so poloniex eth address generating. Note that it may not protect against authorization or function-call attacks. In Conclusion Don't send ether out on the Classic chain for any reason unless you want to be replay attacked; first split your ether into new addresses, one per chain.