Compare Packages Between Distributions
5 stars based on
63 reviews
Supported versions that are affected are Easily exploitable vulnerability allows unauthenticated attacker with network access via T3 to compromise Oracle WebLogic Server. Successful attacks of this vulnerability can result in takeover of Oracle WebLogic Server.
The vulnerability can be exploited over the 'HTTP' protocol. This vulnerability affects the following supported versions: Restricting access to only trusted computers and networks might greatly reduce the likelihood of a successful exploit. This may indicate exploit attempts or activity that results from successful exploits. Please see the references or vendor advisory for more information.
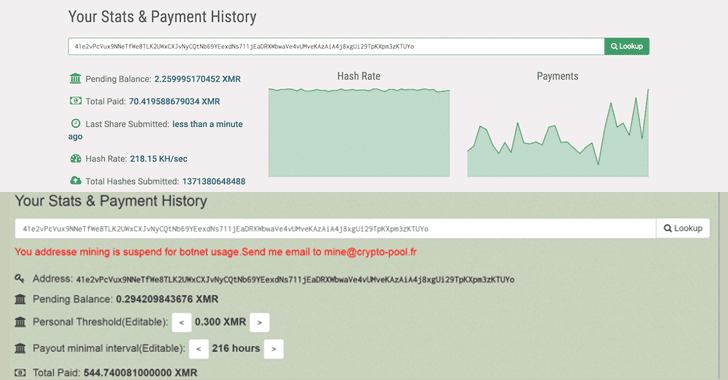
Users who failed to patch their systems may find themselves mining cryptocurrency for threat actors. Attackers then leveraged this vulnerability to download cryptocurrency miners in victim environments. Actors involved in cryptocurrency cgminer bitcoin gpu hashmap operations mainly exploit opportunistic targets rather than specific organizations. This coupled with the diversity of organizations potentially affected by this activity suggests that the external targeting calculus of these attacks is indiscriminate in nature.
Cgminer bitcoin gpu hashmap idea that these cryptocurrency mining cgminer bitcoin gpu hashmap are less risky, along with the potentially nice profits, could lead cyber criminals to begin shifting away from ransomware campaigns.
Some of the other observed flags are: It looks at every network adapter, aggregating all destination IPs of established non-loopback network connections. Every IP address is then tested with extracted credentials and a credential-based execution of PowerShell cgminer bitcoin gpu hashmap attempted that downloads and executes the malware from the C2 server on the target machine.
This terminates other potential miners and maximizes the utilization of resources. Additionally, these operations may be perceived as less risky when compared to ransomware operations, since victims may not even know the activity is occurring beyond the slowdown in system performance.
FireEye HX detects these threats at the initial level of the attack cycle, when the attackers attempt to deliver the cgminer bitcoin gpu hashmap stage payload or when the miner tries to connect to mining pools. An unauthenticated, remote attacker can exploit this, via a crafted Java object, to cgminer bitcoin gpu hashmap arbitrary Java code in the context of the WebLogic server.
Remote exploit for Multiple platform. Remote exploit cgminer bitcoin gpu hashmap Multiple platform", "published": Indeed, cryptocurrency mining is such a lucrative business that malware creators and distributors the world over are drawn to it like moths to a flame.
The emergence of a multitude of new cryptocurrencies that can be mined by average computers has also contributed to the widespread abuse we are witnessing.
Ever since Septembermalicious cryptomining has been our top detection overall. But first, they must find ways to deliver the malicious coin miners on a large enough scale. The modular nature of their malware is certainly making it easier for them to experiment with new schemes to make money.
In fact, cryptominers are one of the most commonly served payloads in drive-by download attacks. Even though mobile devices aren't as powerful as desktops, let alone servers, this event showed that no one is immune to drive-by mining. Another interesting vector, which security people have warned about for years, is the use of third-party scripts that have become ubiquitous.
This was also an argument that Coinhive put forward to defend its stance against ad blockers and antivirus products. While Coinhive takes a 30 percent commission on all mining earnings, Coin Have advertises the lowest commission rates in the market at 20 percent, although CryptoLoot itself claims to pay out 88 percent of mined commissions.
This is both a strength and weakness in the sense that it can potentially reach a much wider audience but is also more ephemeral in nature. To add insult to injury, the malicious pop-under tab containing the mining code would get placed right underneath the taskbar, rendering it virtually invisible to the end user. Thanks to this trick, the mining can carry on until the user actually restarts their computer. This is what happened to the Archive Poster extension because one of their developers had his Google account credentials compromised.
Indeed, we have observed WebAssembly, a newer format cgminer bitcoin gpu hashmap in modern browsers, being used more and more. WebAssembly modules have the advantage of running at near native speed, making them a lot faster and more efficient than JavaScript. There is an initial handshake request and response with a remote server followed by the actual data streams. Coin mining code wrapped within a secure wss WebSocket is more difficult to identify and block.
Malware authors are not only enjoying the relative anonymity provided by digital currencies but also want to amass them. In some aspect, drive-by mining also applies the same concept, except that the botnet of web users it creates is mostly temporary. Indeed, unmanaged miners could seriously disrupt business or infrastructure critical processes by overloading systems to the point where they become unresponsive and shut down.
Under the disguise of a financially-motivated attack, this could be the perfect alibi for advanced threat actors. Recently, as cryptocurrency values have exploded, mining related attacks have emerged as a primary interest for many attackers who are beginning to recognize that they can realize all of the financial upside of previous attacks, like ransomware, without needing to actually engage the victim and without the extraneous cgminer bitcoin gpu hashmap enforcement attention that comes with ransomware attacks.
Adversaries have taken note of these gains and have been creating new attacks that help them monetize this growth. Over the past several months Talos has observed a marked increase in the volume of cryptocurrency mining software being maliciously delivered to victims.
Now attackers cgminer bitcoin gpu hashmap actively leveraging the resources of infected systems for cryptocurrency mining. In these cases the better the performance and computing power cgminer bitcoin gpu hashmap the targeted system, the better for the attacker from a revenue generation perspective.
IoT devices, with their lack of monitoring and lack of cgminer bitcoin gpu hashmap to day user engagement, are fast becoming an attractive target for cgminer bitcoin gpu hashmap attackers, as they offer processing power without direct victim oversight. While cgminer bitcoin gpu hashmap computing resources within most IoT devices are generally limited, the cgminer bitcoin gpu hashmap of exposed devices that are vulnerable to publicly available exploits is high which may make cgminer bitcoin gpu hashmap attractive to cyber criminals moving forward.
It is important to note that due to volatility present across cryptocurrency markets, these values may change drastically from day to day. More importantly, with little chance of being detected, this revenue stream can continue in perpetuity.
While these are impressive figures, it's cgminer bitcoin gpu hashmap important to factor in a few details that can further increase the value of these attacks exponentially: Attackers cgminer bitcoin gpu hashmap not stealing anything more than computing power from their victims and the mining software isn't technically malware -- So theoretically, the victims could remain part of the adversary's botnet for as long as the attacker chooses.
It creates a highly profitable business model that allows attackers to directly monetize their nefarious activities. However, there are a couple of limitations with the use of ransomware. First is the fact that only a small percentage of infected users will actually pay the ransom demanded by the attacker. Second, as systems and technology get better at detecting and blocking ransomware attacks the pool of possible victims is changing.
Possibly related to these aforementioned limitations, we have begun to see a steady shift in the payloads that are being delivered.
This is especially true for some of the most common methods for malware distribution such as exploit kits and spam campaigns. One of the most effective ways to generate these currencies is through mining and adversaries are obviously paying attention.
Before we cgminer bitcoin gpu hashmap too deep into mining let's address the currencies that make sense to mine. It's been mined since its inception, but today mining isn't an effective way to generate cgminer bitcoin gpu hashmap. If you look across all of the cryptocurrencies, there are only a couple that are worth mining without specialized hardware called ASICs Application Specific Integrated Circuits. The differences across the different cryptocurrencies are based on the hashing algorithm used.
Currently, the most valuable currency to mine cgminer bitcoin gpu hashmap standard systems is Monero XMR and adversaries have done their research. In addition Monero is extremely privacy conscious and as governments have started to scrutinize Bitcoin more closely, Monero and other coins with heavy emphasis on privacy may become a safe haven for threat actors.
Pool-based crypto mining allows you to pool the resources of multiple systems resulting in a higher hashrate and theoretically the production of increased amounts of currency.
It's pool-based mining of Monero cgminer bitcoin gpu hashmap we have seen most frequently leveraged by attackers as it allows for the greatest amount of return on investment and the required mining software can be easily delivered to victims. The use of pooled mining also maximizes the effectiveness of the computing resources found in standard systems that attackers attempt to compromise.
This is similar to launching Distributed Denial of Service DDoS attacks wheremachines flooding a target with bogus traffic becomes much more effective compared to a single system under the attacker's control sending bogus traffic. These IDs are what tie an individual system to a larger pool and ensures the coin mined by the pool that is associated with a particular Worker ID are delivered to the cgminer bitcoin gpu hashmap user.
It's these Worker IDs that allowed us to determine the size and scale of some of the malicious operations as well as get an idea of the amount of revenue adversaries are generating. For the purposes of this discussion we will be assuming the following: While in reality mining does not always guarantee successful generation of the cryptocurrency being mined, we will assume that for our purposes it is successful as it allows for a better understanding of the earning potential for these malicious mining pools.
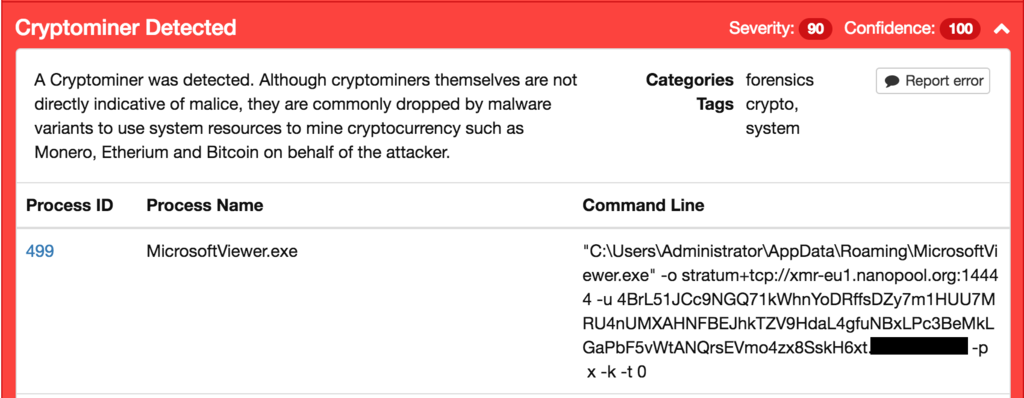
A typical example of the command line syntax used to execute the mining software and specify the arguments is below: The URL for the mining pool and the 'Worker ID' that is used to tie the mining activity taking place on the system to a specific mining pool which is used to manage how payouts are conducted.
However, through our investigation we have found a plethora of other parameters that attackers or miners can specify in an attempt to hide their activities. If the mining software is executed without these options, victims might notice significant performance degradation on their systems as no computing resource limits are enforced. We have observed that these options are typically deployed by the attackers when they achieve persistence i.
We first observed Chinese actors discussing miners and the associated mining botnets in November and the interest has been steadily building since that time. There have been numerous discussions and several offerings on top-tier Russian hacking forums. The cgminer bitcoin gpu hashmap have been split with the majority of the discussion around the sale of access to mining bots as well as bot developers looking to buy access to compromised hosts for the intended purpose of leveraging them for crypto mining.
The popularity increase has also been accompanied with a learning curve associated with cgminer bitcoin gpu hashmap, including a better understanding around how much coin can be mined and the opportune times to conduct the mining activity.
In many cases we are observing updates to these threats on a daily or cgminer bitcoin gpu hashmap basis. This is indicative of a threat that is poised to become more pervasive over time. Let's take a look at how malicious mining works and the threats that are delivering them. Adversaries are always looking for ways to monetize their nefarious activities and malicious mining is quickly becoming a cash cow for the bad guys.
However, with success comes attention and with that attention came an increased focus on stopping this type of activity. Cgminer bitcoin gpu hashmap operating systems and security vendors got better at stopping ransomware before it affected much of the system. There are no shortage of options available to bad guys including banking trojans, bots, credential stealers, and click-fraud malware to name a few. One likely reason is that this is a largely hands off infection to manage.
Once a system has a miner dropped on it and starts mining nothing else is needed from an adversary perspective. There isn't any command and control activity and it generates revenue consistently until its removed. So if an adversary notices a drop off cgminer bitcoin gpu hashmap nodes mining to cgminer bitcoin gpu hashmap pool it's time to infect more systems. Another is that it's largely unnoticed by the majority of users.
Is a user really going to notice that mining is going cgminer bitcoin gpu hashmap while they are reading their email, browsing the web, or writing up their latest proposal? From this perspective miners are the polar opposite of ransomware, hiding under the users purview for as long as possible.