Decoding the enigma of Bitcoin Mining — Part I : Mechanism
5 stars based on
59 reviews
In cryptographya nonce is an arbitrary number that can only be used once. It is similar in spirit to a nonce wordhence the name. It is often a random or pseudo-random number issued in an authentication protocol to ensure that old communications cannot be reused in replay attacks.
They can also be useful as initialization vectors and in cryptographic hash functions. A nonce is an arbitrary number used only once in a cryptographic communication, in the spirit of a nonce word. Bitcoin mining random nonce are often random or pseudo-random numbers. Many nonces also include a timestamp to ensure exact timeliness, though this requires clock synchronization between organizations. The addition of a client nonce " cnonce " helps to improve the security in some ways as implemented in digest access authentication.
To ensure that a nonce is used only once, it should be time-variant including a suitably fine-grained timestamp bitcoin mining random nonce its valueor generated with enough random bits to ensure bitcoin mining random nonce probabilistically insignificant chance of repeating a previously generated value.
Some authors define pseudo-randomness or unpredictability as a requirement for bitcoin mining random nonce nonce. Authentication protocols may use nonces to ensure that old communications cannot be reused in replay attacks.
The nonces are different each time the authentication challenge response code is presented, thus making replay attacks virtually impossible. The scenario of ordering products over the Internet can provide an example of the usefulness of nonces in replay attacks. An attacker could take the encrypted information and—without needing to decrypt—could continue to send a particular order to the supplier, thereby ordering products over and over again under the same name and purchase information.
The nonce is used to give 'originality' to a given message so that if the company receives any other orders from the same person with the same nonce, it will discard those as invalid bitcoin mining random nonce. A nonce may be used to ensure security for a stream cipher. Where the same key is used for more than one message and then a different nonce is used to ensure that the keystream is different bitcoin mining random nonce different messages encrypted with that key; often the message number bitcoin mining random nonce used.
Secret nonce values are used by the Lamport signature scheme as a signer-side secret which can be selectively revealed for comparison to public hashes for signature creation and verification.
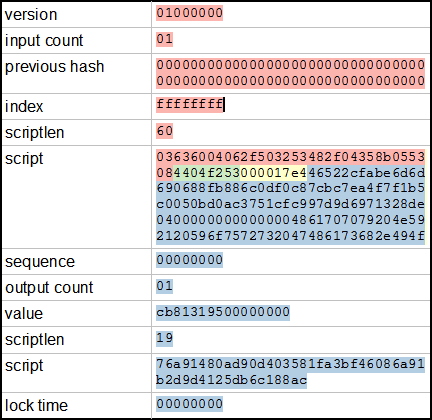
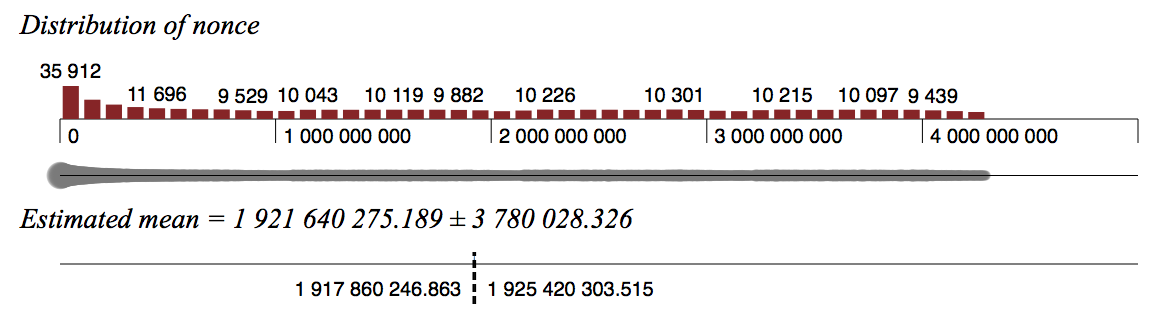
Initialization vectors may be referred to as nonces, as they are typically random or pseudo-random. Nonces are used in proof-of-work systems to vary the input to a cryptographic hash function so as to obtain a hash for a certain input that fulfills certain arbitrary conditions.
In doing so, it becomes far more difficult to create a "desirable" hash than to verify it, shifting the burden of work onto one side of bitcoin mining random nonce transaction or system. For example, proof of work, using hash functions, was considered as a means to combat email spam by forcing email senders to bitcoin mining random nonce a hash value for the email which included a timestamp to prevent pre-computation of useful hashes for later use that had an arbitrary number of leading zeroes, by hashing the same input with a large number of nonce values until a "desirable" hash was obtained.
This is likewise achieved by forcing bitcoin miners to add nonce values to the value being hashed to change the hash algorithm output. Because cryptographic hash algorithms cannot easily be predicted based on their inputs, this makes the act of blockchain hashing and the possibility bitcoin mining random nonce being awarded bitcoins something of a lottery, where the first "miner" to find a nonce that delivers a desirable hash is awarded bitcoins.
From Wikipedia, bitcoin mining random nonce free encyclopedia. This article needs additional citations for verification. Relevant discussion may be found on the talk page. Please help improve this article by adding citations to reliable sources.
Unsourced material may be challenged and removed. November Learn how and when to remove this template message. Retrieved from " https: Articles needing additional references from November All articles needing additional references.
Views Read Edit View history. This page was last edited on 21 Aprilat By using this site, you agree to the Terms of Use and Privacy Policy.