What s a bitcoin miner virus scanner

Click the Finish button to complete the installation process and launch CCleaner. Discover more about our award-winning security. Step 9 Click the Yes button when CCleaner prompts you to backup the registry. In our security solutions stopped the launch of Web miners on more than 70 million occasions, and the use of such scripts is only set to rise.

Run a malware scan from time to time to defend yourself against Bitcoin miner malware in the future. Users look for this type of software on peer-to-peer networks and download it intentionally. Similar to most other malware programs, it is next to impossible to identify when the Bitcoin miner malware takes control of your system because it will imitate another program—such as a browser or a Windows application—so as to not to be found.

Click the Yes button. Our experts recently detected a botnet consisting of an estimated several thousand computers on which the Minergate miner was secretly installed. In just a few clicks, you can get a FREE trial of one of our products — so you can put our technologies through their paces. Free protection for your computers.
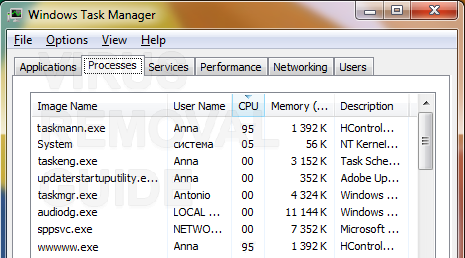
Jay Geater Last Updated: To remove Bitcoin Miner from your Windows installed programs, you need to perform the following steps:. Note that a rank-and-file user can install a miner application intentionally, to mine cryptocurrency on their own.

Step 12 After the Installation completes, click the Finish button. Step 4 Right-click on Bitcoin Minerand then click Uninstall. To remove Bitcoin Miner from your Windows installed programs, you need to perform the following steps:.

Step 12 After the Installation completes, click the Finish button. Cryptocurrency mining is an IT industry buzzword and a rapidly growing phenomenon. If you feel your browser is infected with Bitcoin Miner, you should reset it to its original state when it was freshly installed. To give you an idea of the scale of this phenomenon: And although in some cases ordinary miners can be installed by users on purpose, Web miners are most certainly intrusive and need to be blocked.
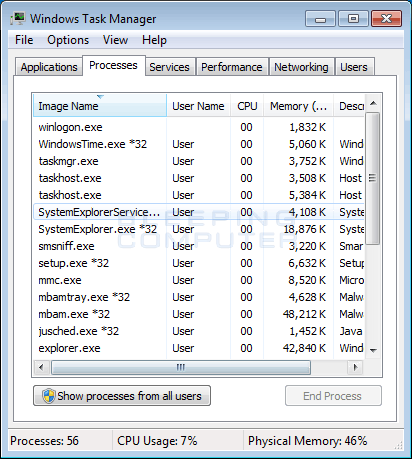
Note that a rank-and-file user can install a miner application intentionally, to mine cryptocurrency on their own. Step 3 In the installed programs list, locate the listing for Bitcoin Miner. So if you have any of our latest security solutions installed, rest assured that the AV will find and stop all Web miners. Company Names Detection Names.
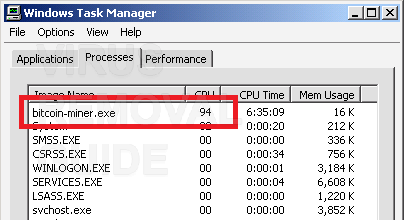
From ransomware to Web miners. They use Telegram channels devoted to online work opportunities; you might come across ads offering trial versions of such droppers for distributing a hidden miner. Step 12 Click the Close button after CCleaner reports that the issues have been fixed.

Distinguishing legal mining from illegal activity is the challenge. Step 6 Once Internet Explorer completes the resetting tasks, click the Close button. It essentially overloads the processor and video card, slowing down the machine, so you might experience lags and freezes while trying to use it for everyday tasks.

You can learn more about Unwanted Applications here. The most common Web miner, and the one used in the vast majority of cases, is CoinHive. Step 6 Click the Registry button in the CCleaner main window. Microsoft Gold Certified Company Recognized for best-in-class capabilities as an ISV Independent Software Vendor Solvusoft what s a bitcoin miner virus scanner recognized by Microsoft as a leading Independent Software Vendor, achieving the highest level of completence and excellence in software development.