Mimikatz 20 export private key bitcoin

Mimikatz supports both Windows bit and bit and allows you to gather various credential types, using various techniques:. As the attackers moved, they continued to install the KillDisk malware for use at a later time, and where necessary, set up SSH backdoors to ensure persistent remote access, just in case. Recently, Microsoft released the Anniversary update and, with it, the Remote Credential Guarda security feature that aims to protect credentials over Remote Mimikatz 20 export private key bitcoin RDP connections by generating the necessary service tickets from the source machine instead of by copying the credentials hashes and TGTs to the target machine. However, because service tickets Ticket Granting Service are not encrypted, it is still possible to pass them to gain access to specific services SPN.

Even three months following the attack, workers must still manually control the breakers at the impacted substations. On December 23,the western region of Ukraine experienced a sweeping blackout. This can be done in a few ways, two of which include:

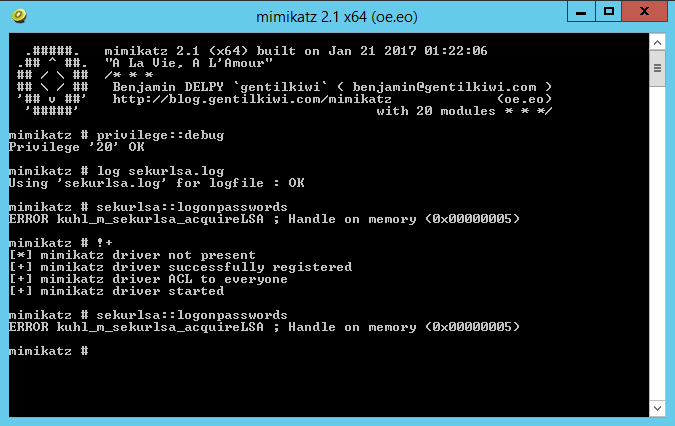
Exploiting Mimikatz 20 export private key bitcoin Mode to Escalate an Attack This example explains how Safe Mode can be exploited to allow an attacker to capture user credentials and execute pass-the-hash attacks to achieve lateral movement. The first step in gaining access to LSA Secrets is to grant the local administrator access to the Security registry hive. Based on tests conducted by CyberArk Labs, we found this technique to be highly effective in stealthily enabling lateral movement.
This can be done in a few ways, two of which include:. Given the limitations of Remote Credential Guard, what else can be done to protect derived credentials from theft? As the power went out throughout the Ukraine, the system operators were left without the ability to take back control of their machines and stop the attack. So, is this the end mimikatz 20 export private key bitcoin credential theft attacks? As the attackers moved, they continued to install the KillDisk malware for use at a later time, and where necessary, set up SSH backdoors to ensure persistent remote access, just in case.
Attackers can create a malicious service that is configured to load in Safe Mode. This can easily be done in a variety of ways, including directly from the command line in Normal Mode. So, is this the end of credential theft attacks?

To successfully execute a pass-the-hash attack, the compromised credential hash must still be valid. Two of the three electricity providers in the area fell victim to a cyber attack that shut off electricity throughout the region and purposely made remediation extremely difficult. If the victim machine did not contain any services with domain controller access, we wanted to be mimikatz 20 export private key bitcoin to laterally move to other machines, which may contain services with higher privileges.
This blog will explore some of the ways this attack vector can be executed. Using compromised credentials, the attackers logged into the VPN to remotely connect to workstations in the control room. It seems to be replacing the Restricted Admin modea feature introduced in Windows 8. The Proof of Concept Because this specific risk involves the compromise of service credentials, we hypothesized that these service credentials — mimikatz 20 export private key bitcoin are used for legitimate services — could potentially be captured and injected into a malicious service, thus granting an attacker access to all systems and resources to which the original service had access.
