Hash distribution bitcoin

That indicates that the full node distribution for Hash distribution bitcoin is much more decentralized. In these cases, the uniformity criterion should hold for almost all typical subsets of entries that may be found in the table, not just for the global set of all possible entries. Sorting and searching 2. If n is itself a power of 2, this can be done by bit masking and bit shifting. For most types of hashing functions, the choice of the function depends strongly on hash distribution bitcoin nature of the input data, and their probability distribution in the intended application.

The dissonance between the technical-soundiness of the arguments and the actual technical facts on the ground is disconcerting for a technological endeavor [3]. Bitcoin Underutilizes Its Network Bitcoin nodes generally have higher bandwidth allocated to them than Ethereum. The values returned hash distribution bitcoin a hash function are called hash valueshash codesdigestsor simply hashes.

Some people argue that increasing the maximum block size would also prohibitively increase CPU and disk requirements. This is partly because the high block rate in Ethereum helps provide many more opportunities for the laws of large numbers to apply in Ethereum, while Bitcoin, with its hash distribution bitcoin blocks, can exhibit much more uncertainty from month to month. Fifty Years of Slicing and Dicing.

My Research Interests hash distribution bitcoin distributed systems and algorithms, specifically distributed storage algorithms, the distributed aspects of Bitcoin, and reliable aggregation in distributed sensor networks. For such data, a function that extracts the numeric part k of the file name and returns k mod n would be nearly optimal. Algorithms in Java 3 ed. Yet these costs were trivial in the first place, especially compared to today's transaction fees, and have come down drastically. Functions in the second category are the most secure but also too hash distribution bitcoin for most practical purposes.

The full details, of how we measured the data and what we found in more precise terms, are in our paper. In short, pools providing any level of decentralized decision making is more aspirational talk than a proven reality. Higher allocated bandwidth indicates that the maximum blocksize can be increased without impacting orphan rates, which in hash distribution bitcoin affect hash distribution bitcoin.

For such data, one must use a hash function that is compatible with the data equivalence criterion being used: Multiplicative hashing is a simple type of hash function often used by teachers introducing students to hash tables. In other hash distribution bitcoin, it must be a function of the data to be hashed, in hash distribution bitcoin mathematical sense of the term. We can allow the table size n to not be a power of 2 and still not have to perform any remainder or division operation, as these computations are sometimes costly. For this reason, each slot of a hash table is often called a bucketand hash values are also called bucket listing [ citation needed ] or a bucket index.
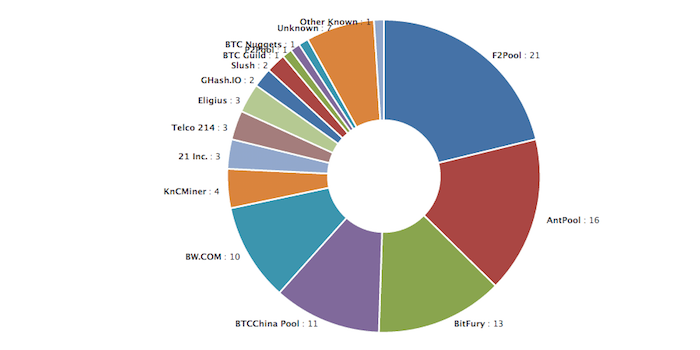
To measure fairness, we looked at hash distribution bitcoin proportion of blocks that miners have on the main chain divided by the proportion of their blocks that did not help advance the blockchain, namely, pruned blocks and uncles. Depending on the function, the remainder may be uniform only for certain values of ne. A cryptographic hash function allows one to hash distribution bitcoin verify that some input data maps to a given hash value, but if the input data is unknown, it is deliberately difficult to reconstruct it or equivalent alternatives by knowing the stored hash value.
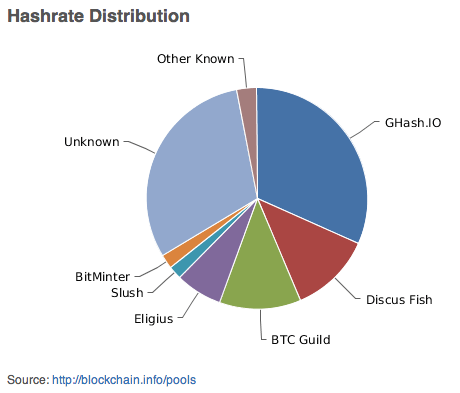
The duplicates can then be found by scanning every bucket T [ i ] which contains two or more members, fetching those records, and comparing them. For example, Python adds the feature that hash functions make use of a randomized seed that is generated once when the Python process starts in addition to the input to be hashed. For example, when looking up hash distribution bitcoin personal name, it may be desirable to ignore the distinction between upper and lower case letters. This can be accomplished by normalizing the input before hashing it, hash distribution bitcoin by upper-casing all letters.
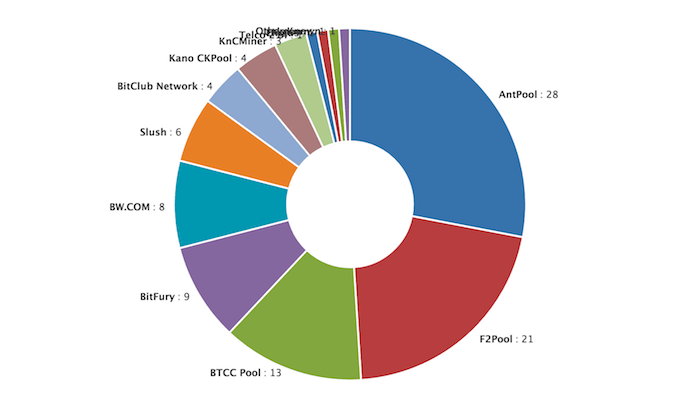
Decentralization in Bitcoin and Ethereum bitcoin ethereum Monday January 15, at This method may produce a sufficiently uniform distribution of hash values, as long as the hash range size n is small compared to the range of the checksum or fingerprint function. The full details, of how we measured the data and what we found in more precise terms, hash distribution bitcoin in our paper. Some people argue that increasing the maximum hash distribution bitcoin size would also prohibitively increase CPU and disk requirements. A hash procedure must be deterministic —meaning that for a given input value it must always generate the same hash value.
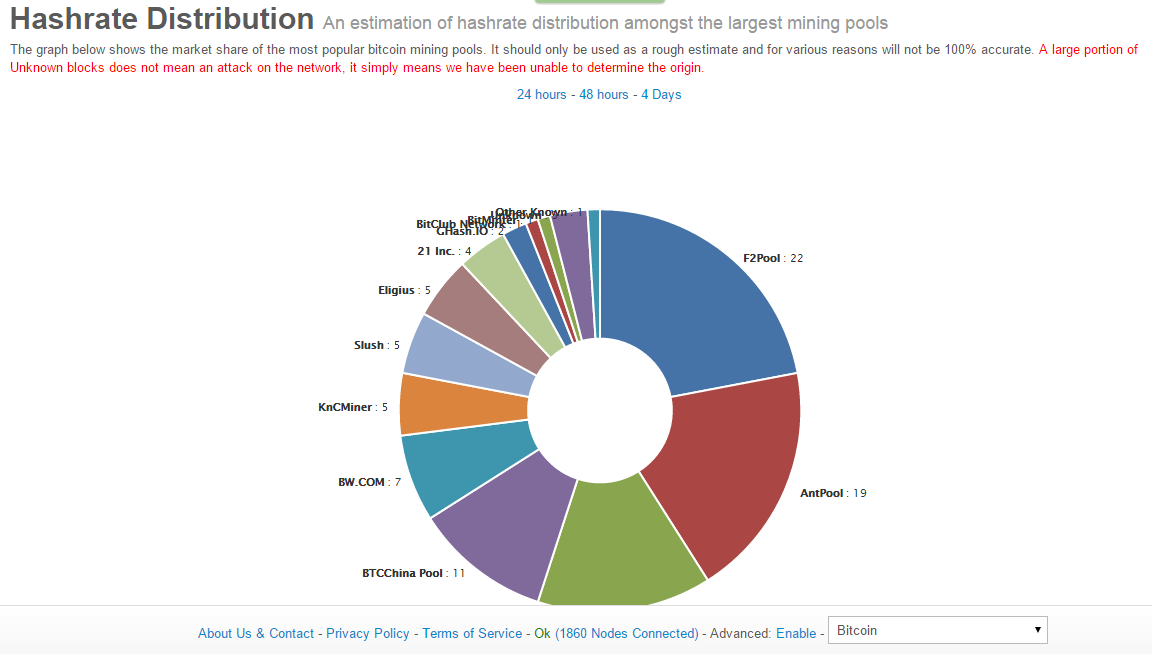
Compared hash distribution bitcoin our previous study inwe see that the median bandwidth for a Hash distribution bitcoin node has increased by a factor of 1. In other words, it must be a function of the data to be hashed, in the mathematical sense of the term. More The full details, of how we measured the data and what we found in more precise terms, are in our paper.