Bitiodine extracting intelligence from the bitcoin network propagation
To receive news and publication updates for Security and Communication Networks, enter your email address in the box below. Bitcoin Privacy Bitcoin has also recently received considerable interest regarding the security and anonymity in security research. Prudent practices for designing malware experiments:

View at Google Scholar. View at Google Scholar M. An analysis of rogue AV campaigns - Cova, Leita, et al. View at Google Scholar C.
. Secure Multiparty Computations on Bitcoin..jpg)
View at Google Scholar C. Bitcoin Privacy Bitcoin has also recently received considerable interest regarding the security and anonymity in security research. Decoy resources have also been recently used to improve the security of hashed passwords [20] and to detect illegally obtained data from file hosting services [28]. Moreover, these reports mainly focus on the advancements in ransomware attacks and their levels of sophistication, rather than providing

Exposing the lack of privacy in file hosting services - Nikiforakis, Balduzzi, et al. Nakamoto, Bitcoin, A peer-to-peer electronic cash system, https: View at Google Scholar J.

Decoy resources have also been recently used to improve the security of hashed passwords [20] and to detect illegally obtained data from file hosting services [28]. Based on our analysis, we conclude that detecting and stopping a large number of destructive ransomware attacks is not as complex as it has been reported and deploying practical defense mechanisms a However, designing effective defense mechanisms is not p

In order to monitor the file system activity, multiple approaches could be used. In our definition, monitoring decoy files can be an additional layer of defense on the top of file system activity monitoring to detect ransomware attacks. Nakamoto, Bitcoin, A peer-to-peer electronic cash system, https: Show Context Citation Context View at Google Scholar D.

View at Scopus X. View at Google Scholar X. Security and Communication Networks. In our definition, monitoring decoy files can be an additional layer of defense on the top of file system activity monitoring to A measurement analysis of a large anonymous online marketplace - Christin - Show Context Citation Context
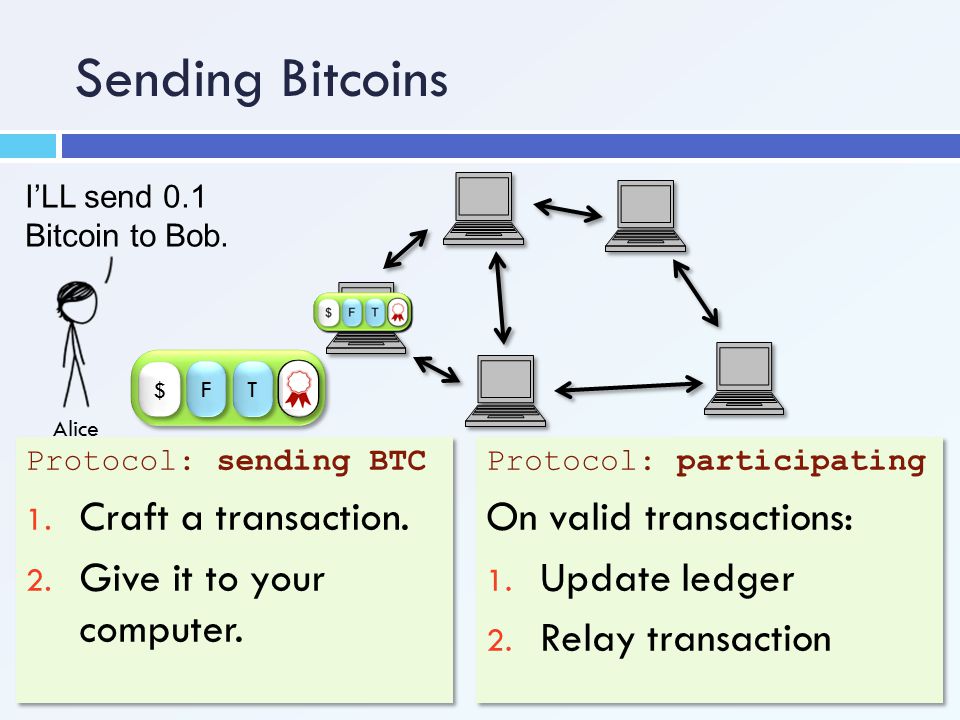
Anonymity of bitcoin transactions: Press, Los Alamitos, CA, Cutting the Gordian Knot: Bitcoin Privacy Bitcoin has also recently received considerable interest regarding the security and anonymity in security research. Nakamoto, Bitcoin, A peer-to-peer electronic cash system, https:

View at Google Scholar X. Lewis and et al. View at Google Scholar A.

Lewis and et al. Given the significant growth of ransomware attacks [37], it is very important to develop a protection technique against this type of malware. Stallings, Network and Internetwork Security: