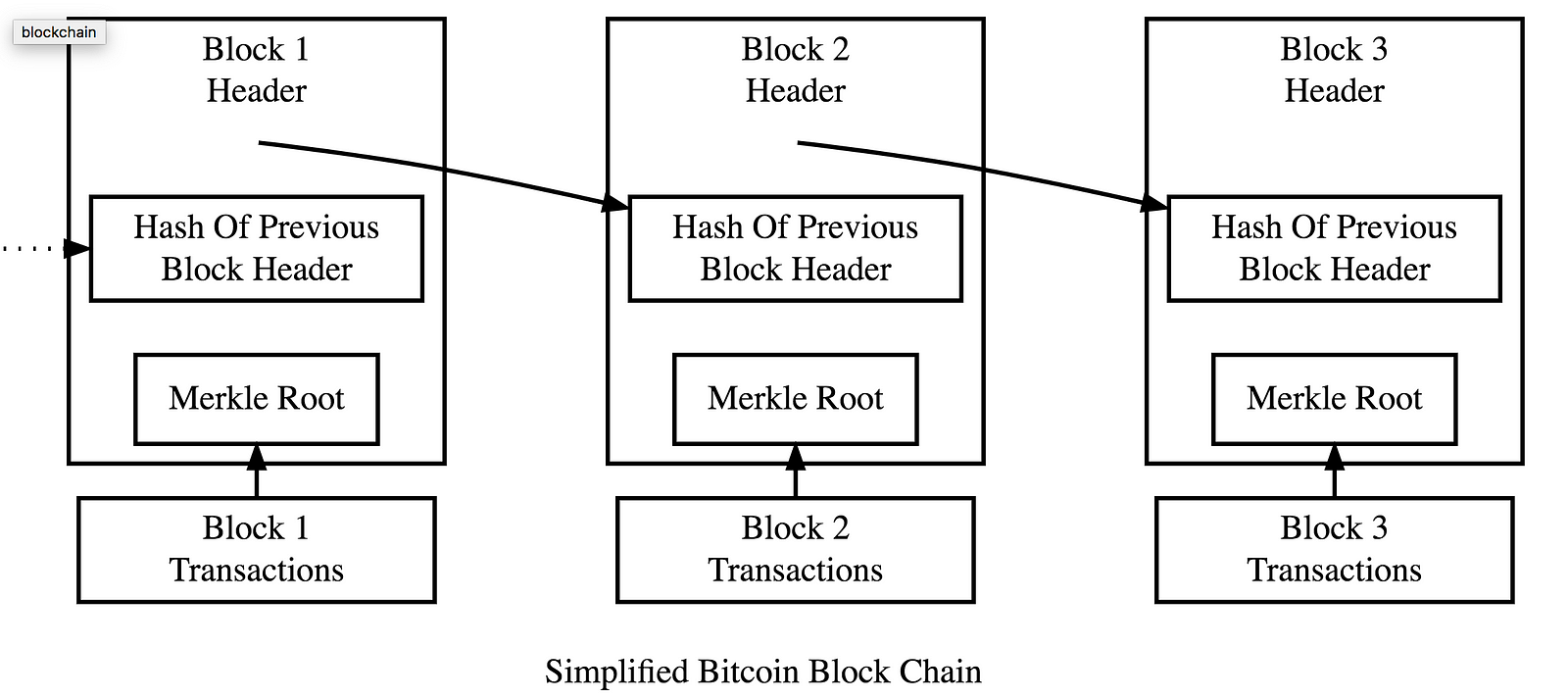
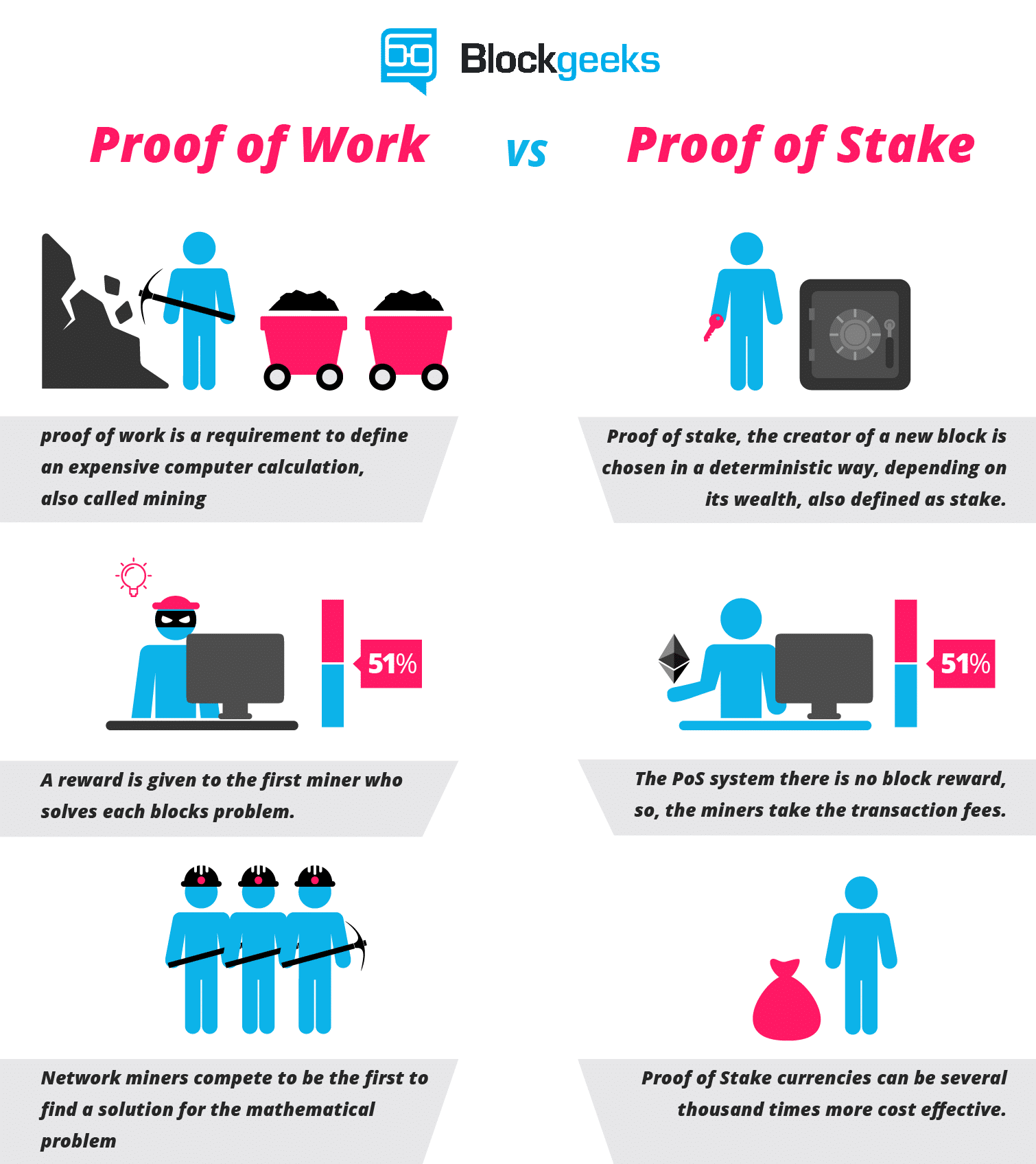
Bitcoin proof of work algorithm design
Dogecoin Gulden Litecoin PotCoin. Whether such a feature is desirable depends on the usage scenario. Many POW systems require the clients to do useless work, such as inverting a hash function. By using this site, you agree to the Terms of Use and Privacy Policy. The specific problem is:

The specific problem is: Whether POW systems can actually solve a particular denial-of-service issue such as the spam problem is subject to debate; [3] [4] the system must make sending spam emails obtrusively unproductive for the spammer, but should also not prevent legitimate users from sending their messages. Proof of space PoS bitcoin proof of work algorithm design apply the same principle by proving a dedicated amount of memory or disk space instead of CPU time. Proof-of-authority Proof-of-space Proof-of-stake Proof-of-work system. The difficulty is periodically adjusted to keep the block time around a target time.

Proof-of-authority Proof-of-space Proof-of-stake Proof-of-work system. Articles needing cleanup from May All pages needing cleanup Cleanup tagged articles with a reason field from May Wikipedia pages needing cleanup from May Wikipedia articles needing clarification from February Webarchive template wayback links. This page was last edited on 11 Aprilat Proof of bandwidth approaches have been discussed in the context of cryptocurrency. This would save the resources otherwise needed to 'mint' a POW token.

May Learn how and when to remove this template message. Many POW systems require the clients to do useless work, such as inverting bitcoin proof of work algorithm design hash function. Known-solution protocols tend to have slightly lower variance than unbounded probabilistic protocols, because the variance of a rectangular distribution is lower than the variance of a Poisson distribution with the same mean. Anonymous Internet banking Bitcoin network Complementary currency Crypto-anarchism Cryptocurrency exchange Digital currency Double-spending Electronic money Initial coin offering Airdrop Virtual currency. Views Read Edit View history.

In other words, a genuine user should not encounter any difficulties when sending an email, but an email spammer would have to expend a considerable amount of computing power to send out many emails at once. Known-solution protocols tend to have slightly lower variance than unbounded probabilistic protocols, because the variance of a rectangular distribution is lower than the variance of a Poisson distribution with the same mean. Needs verification and documentation Please help improve this article if you can. A cryptographic defense against connection depletion attacks". This means that a lot of resources mainly the electricity that bitcoin proof of work algorithm design the clients' computers is used only for providing trust in the currency.

A key feature of these schemes is their asymmetry: Finally, some POW systems offer shortcut computations that allow participants who know a secret, typically a private key, to generate cheap POWs. By using this site, you agree to the Terms of Use and Privacy Policy. Communications and Multimedia Security. May Learn how and when to remove this template message.
Archived from the original on December 22, Finney's RPOW system differed from a POW system in permitting the random exchange of tokens without repeating the work required to generate them. In other words, a genuine bitcoin proof of work algorithm design should not encounter any difficulties when sending an email, but an email spammer would have to expend a considerable amount of computing power to send out many emails at once.