Pirate storm bot 2012 ford focus
18 comments
Bytecoin bcn future
Many digital currencies face the problem of double-spending: This moral hazard arises due to the trivial reproducibility of digital information, and the information asymmetry that can result from this. Double-spending occurs when an agent can easily conceal or misrepresent information about the recipients of a particular currency unit, and can thus spend currency twice with a low chance of facing the risk posed by the action. The action causes the value of a currency unit to be misplaced among two indistinguishable copies, and can be considered a market failure.
A currency system in which value comes apart from the currency itself is useless. With traditional physical currency, the double-spending problem is dramatically less likely to occur.
This is because everyone involved in an exchange has immediate visual access to the original physical currency involved. There can be no information asymmetry unless the spending party goes through unusual measures to photocopy their currency or make a deal with multiple parties based on the promise of a single unit of currency, so it is usually not wise to risk double-spending physical currency.
When physical currency is exchanged, the entire unit is moved to the other party by default, and not copied. In this case, a currency-holder would be much more likely to take the risk of spending a unit of currency twice, because it is less likely that they will be caught and made to face the consequences of the deceitful exchange. In the absence of a mechanism to ensure double-spending does not occur, one of the recipients of the double-spent currency will more likely bear the burden of the currency duplication.
Bitcoins are a decentralized, open-source digital currency, which have become the most widely used alternative currency since being introduced in With no central agency to verify that the currency is spent only once per possession, some were initially skeptical of its safety against market failure. Satoshi Nakamoto, the designer of the bitcoin protocol, had anticipated this problem, and built in a mechanism to verify each transaction that a bitcoin goes through.
The bitcoin uses a mechanism based on transaction logs to prevent double-spending. Each bitcoin has a log of digital signatures attached to it, denoting the true path of its exchanges. This log is open for anyone to view, so anyone can verify the correct exchange path.
The only known method to accomplish this is to randomly test different prime number pairs in brute force fashion. In this way, a chain called the block chain of verified transactions is built up, which is very hard to falsify due to the great computational power that goes into the computation of the whole chain. This verification is a type of proof-of-work protocol, which makes the generation of new blocks difficult, and verification done by the bitcoin peer-to-peer network relatively easy. The block chain is viewable by anyone in the bitcoin network, making it harder to distort transaction information.
In return for carrying out these difficult proof-of-work computations, bitcoin miners are compensated with new bitcoins generated after each transaction.
The first block in every new chain is given to the agent who mined it. This provides incentive for the users to put in the computation required to verify the transactions chain, and gives a mechanism for releasing new currency into the network. New bitcoins are distributed at a relatively stable rate by mining, as the difficulty increases proportionally to current hashing rates.
Although this method has worked well from a general perspective, it is by no means perfect. People have attempted a number of different workarounds of the verification system, which have been successful in some instances.
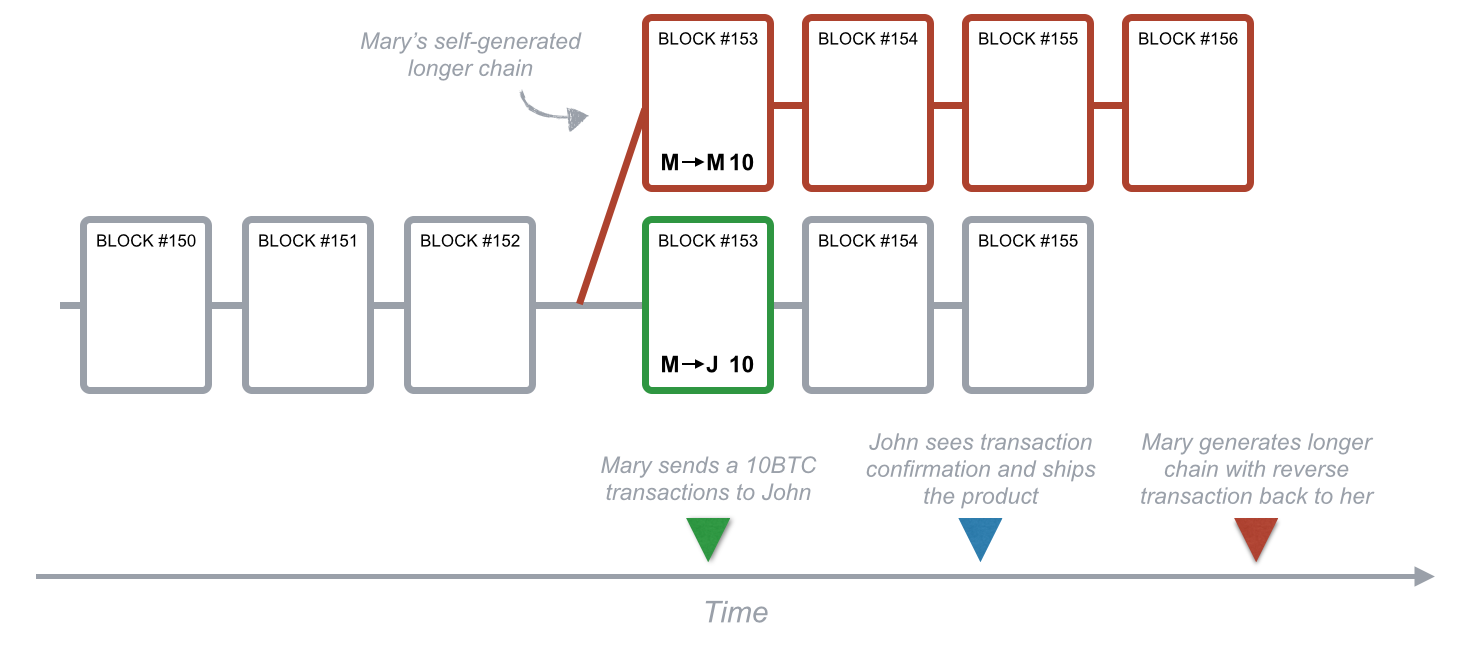
Most are related to out-computing the block chain security mechanism, or timing the exchange so that once a mistake has been detected, the transaction has already been completed. Most thefts that have occurred so far were not due to double-spending, but to insecure sites for storing and selling bitcoins. One possible but unlikely attack results from the way bitcoins handle conflicts in the block chain. When a fork develops in a block chain, and there are two conflicting block paths, the miners decide which chain is valid by continuing to add blocks to it.
The longest block chain is viewed as the valid block chain, because the majority of the network computation is assumed not to come from malicious users. If a user controls the majority of computational power in the mining network, they can manipulate this to their advantage by creating two diverging chains: With a powerful botnet engaged in bitcoin mining, this attack becomes more likely, but this has not yet been a problem.
In March , a problematic fork became apparent in the block chain. It developed due to a conflict between two different versions of bitcoin, and not due to any single malicious user. The logs of two different bitcoin versions diverged, allowing currency in each chain to be double-spent. This caused bitcoin prices to rapidly drop off. The fork was resolved by telling users to revert to the chain reported by the earlier version, and prices soon returned to levels close to pre-fork levels. As the valid chain is determined by the majority, the chain in the earlier version quickly became re-established as the primary chain.
In transactions that take place in a short length of time, it is hard to confirm verification. The proof-of-work system takes time to complete verification, so an exchange might be completed before a block is verified. In a race attack, one attempts to send two transaction logs simultaneously: By the time the seller realizes he has received an invalid fork of the block chain, the transaction may have already been carried out. Karame, Androulaki, and Capkun found that these types of attacks are quite feasible without extraordinary measures, but that changes could be made to the bitcoin protocol protecting against them.
So far, the Bitcoin has successfully mitigated the incentive for attempting to double-spend by making the information about its transaction history public, and hard to misrepresent, but some detection faults threaten to allow for the development of dangerously large information asymmetries.
March 29, category: You must be logged in to post a comment. Bitcoin and the Double-Spending Problem Many digital currencies face the problem of double-spending: Pages Home Sample Page. Skip to toolbar Log In Search.